
You are viewing documentation for KubeSphere version:v3.0.0
KubeSphere v3.0.0 documentation is no longer actively maintained. The version you are currently viewing is a static snapshot. For up-to-date documentation, see the latest version.
Create Workspaces, Projects, Accounts and Roles
This quickstart demonstrates how to create workspaces, roles and user accounts which are required for other tutorials. Meanwhile, you will learn how to create projects and DevOps projects within your workspace where your workloads are running. After this tutorial, you will become familiar with the multi-tenant management system of KubeSphere.
Prerequisites
KubeSphere needs to be installed in your machine.
Estimated Time
About 15 minutes.
Architecture
The multi-tenant system of KubeSphere features three levels of hierarchical structure which are cluster, workspace and project. A project in KubeSphere is a Kubernetes namespace.
You are required to create a new workspace to work with instead of using the system workspace where system resources are running and most of them are viewable only. In addition, it is strongly recommended different tenants work with corresponding roles in a workspace for security considerations.
You can create multiple workspaces within a KubeSphere cluster. Under each workspace, you can also create multiple projects. Each level has multiple built-in roles. Besides, KubeSphere allows you to create roles with customized authorization as well. The KubeSphere hierarchy is applicable for enterprise users with different teams or groups, and different roles within each team.
Hands-on Lab
Step 1: Create an account
After KubeSphere is installed, you need to add different users with varied roles to the platform so that they can work at different levels on various resources. Initially, you only have one default account, which is admin, granted the role platform-admin. In the first step, you create an account user-manager and further create more accounts as user-manager.
-
Log in to the web console as
adminwith the default account and password (admin/P@88w0rd).Tip
For account security, it is highly recommended that you change your password the first time you log in to the console. To change your password, select User Settings in the drop-down menu in the top right corner. In Password Setting, set a new password. You also can change the console language in User Settings.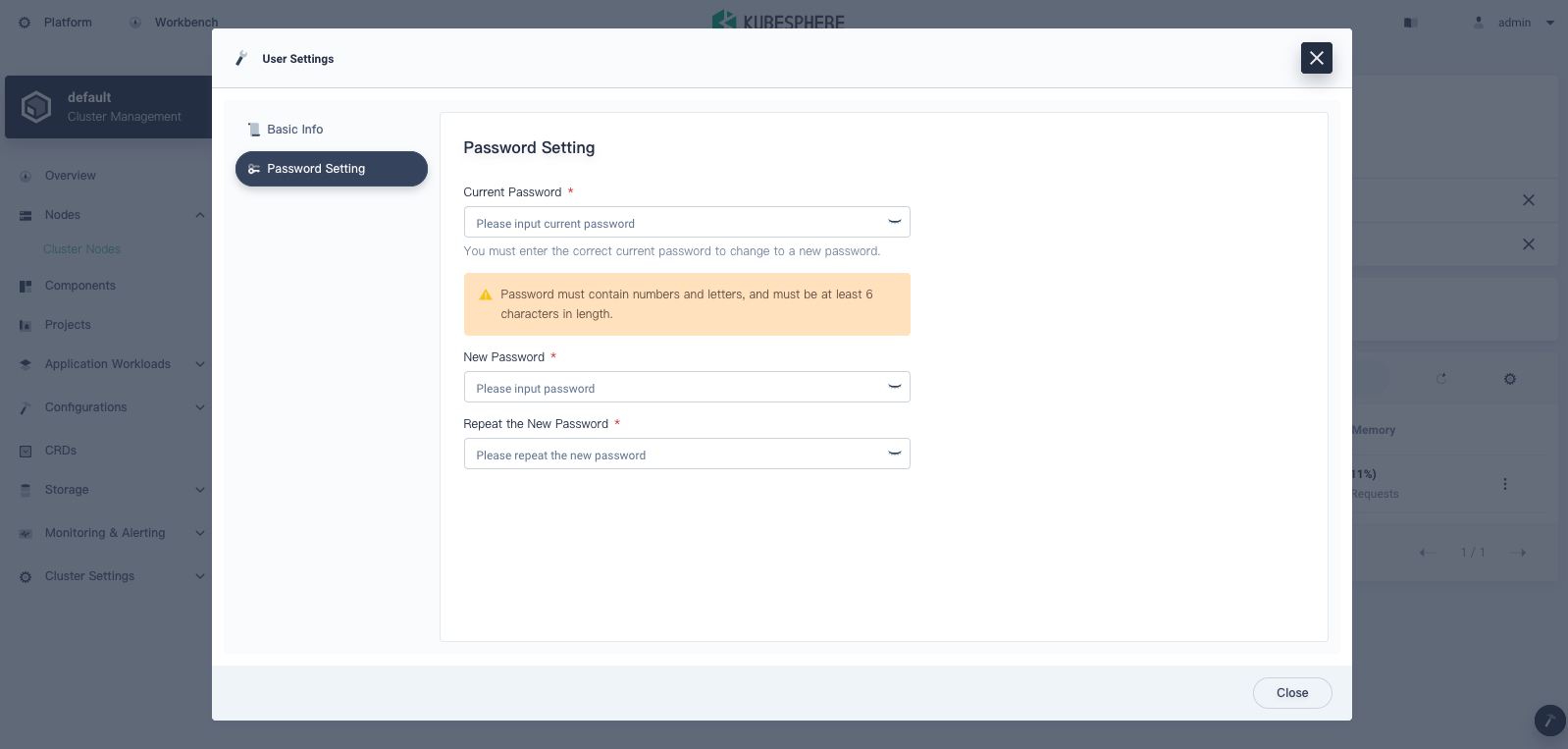
-
After you log in to the console, click Platform in the top-left corner and select Access Control.

In Account Roles, there are four available built-in roles as shown below. The account to be created next will be assigned the role
users-manager.Built-in Roles Description workspaces-managerThe workspace manager on the platform who manages all workspaces on the platform. users-managerThe user manager on the platform who manages all users. platform-regularThe normal user on the platform who has no access to any resources before joining a workspace or cluster. platform-adminThe platform administrator who can manage all resources on the platform. Note
Built-in roles are created automatically by KubeSphere and cannot be edited or deleted. -
In Accounts, click Create. In the pop-up window, provide all the necessary information (marked with *) and select
users-managerfor Role. Refer to the image below as an example.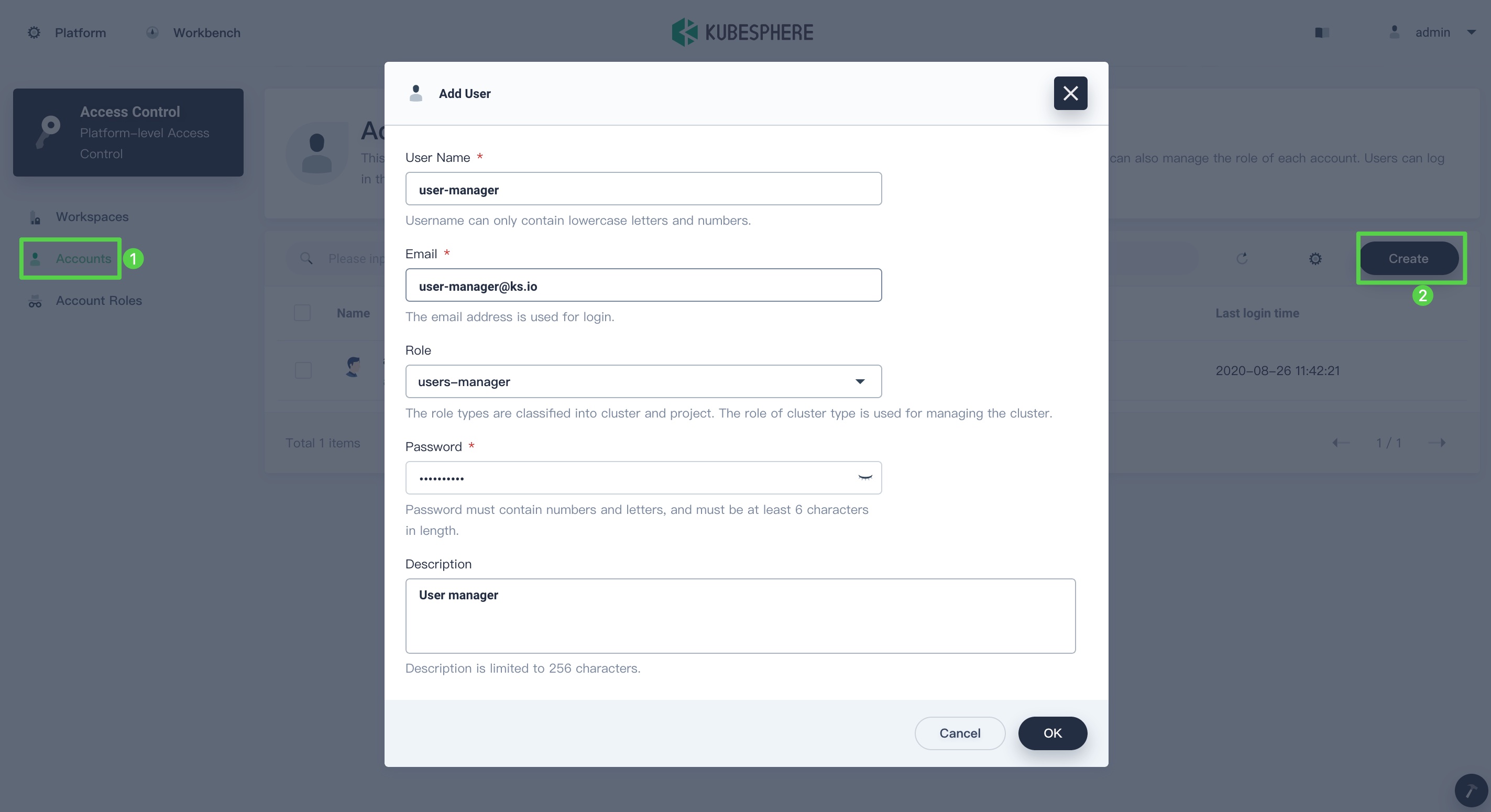
Click OK after you finish. A newly-created account will display in Accounts.
-
Log out of the console and log back in with the account
user-managerto create four accounts that will be used in other tutorials.Tip
To log out, click your username in the top-right corner and select Log Out.Account Role Description ws-managerworkspaces-managerCreate and manage all workspaces. ws-adminplatform-regularManage all resources in a specified workspace (This account is used to invite new members to a workspace in this example). project-adminplatform-regularCreate and manage projects and DevOps projects, and invite new members into the projects. project-regularplatform-regularproject-regularwill be invited to a project or DevOps project byproject-admin. This account will be used to create workloads, pipelines and other resources in a specified project. -
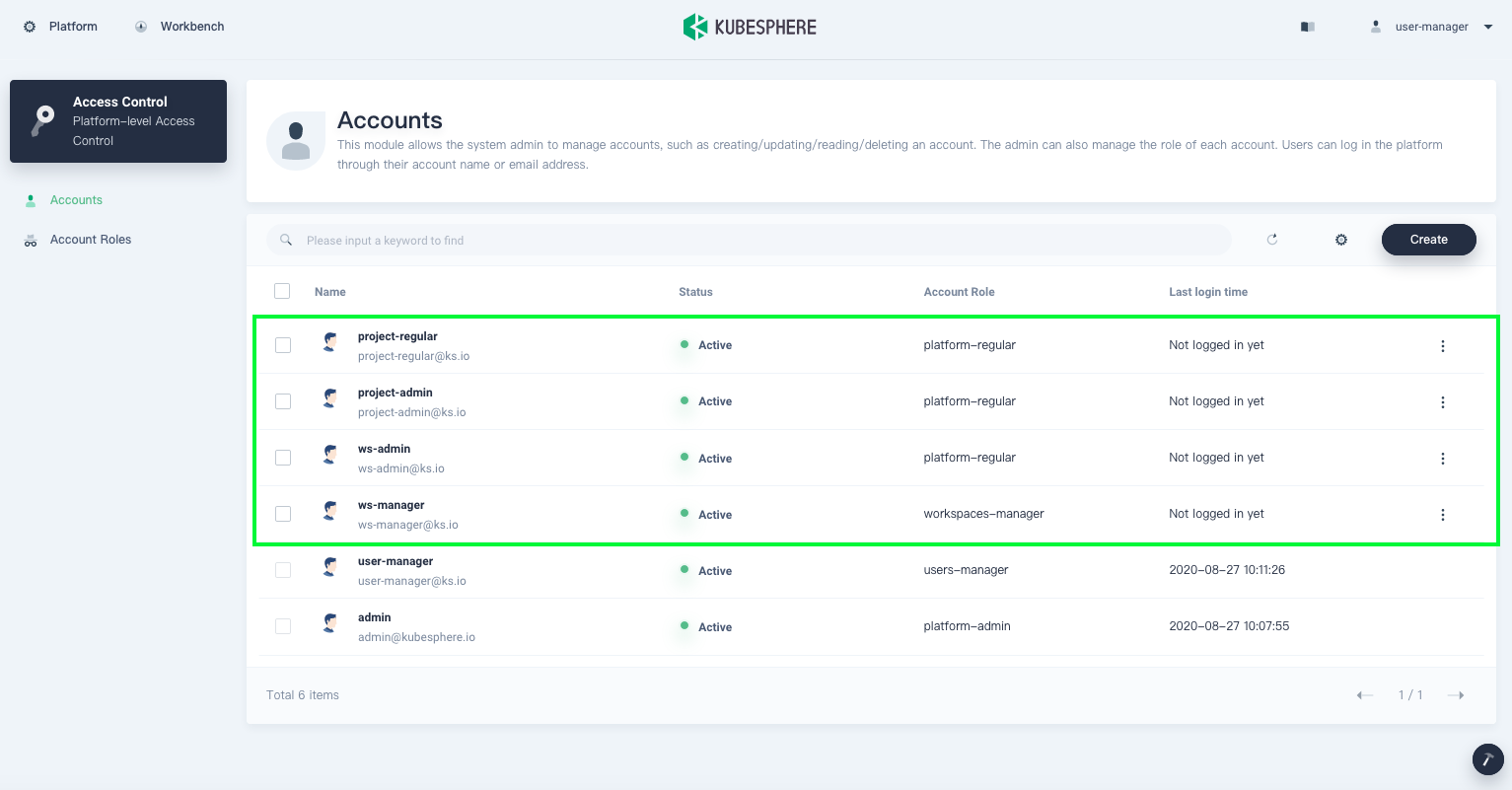
Verify the four accounts created.
Step 2: Create a workspace
In this step, you create a workspace using the account ws-manager created in the previous step. As the basic logic unit for the management of projects, DevOps projects and organization members, workspaces underpin the multi-tenant system of KubeSphere.
-
Log in to KubeSphere as
ws-managerwhich has the permission to manage all workspaces on the platform. Click Platform in the top-left corner and select Access Control. In Workspaces, you can see there is only one default workspacesystem-workspacelisted, where system-related components and services run. You are not allowed to delete this workspace.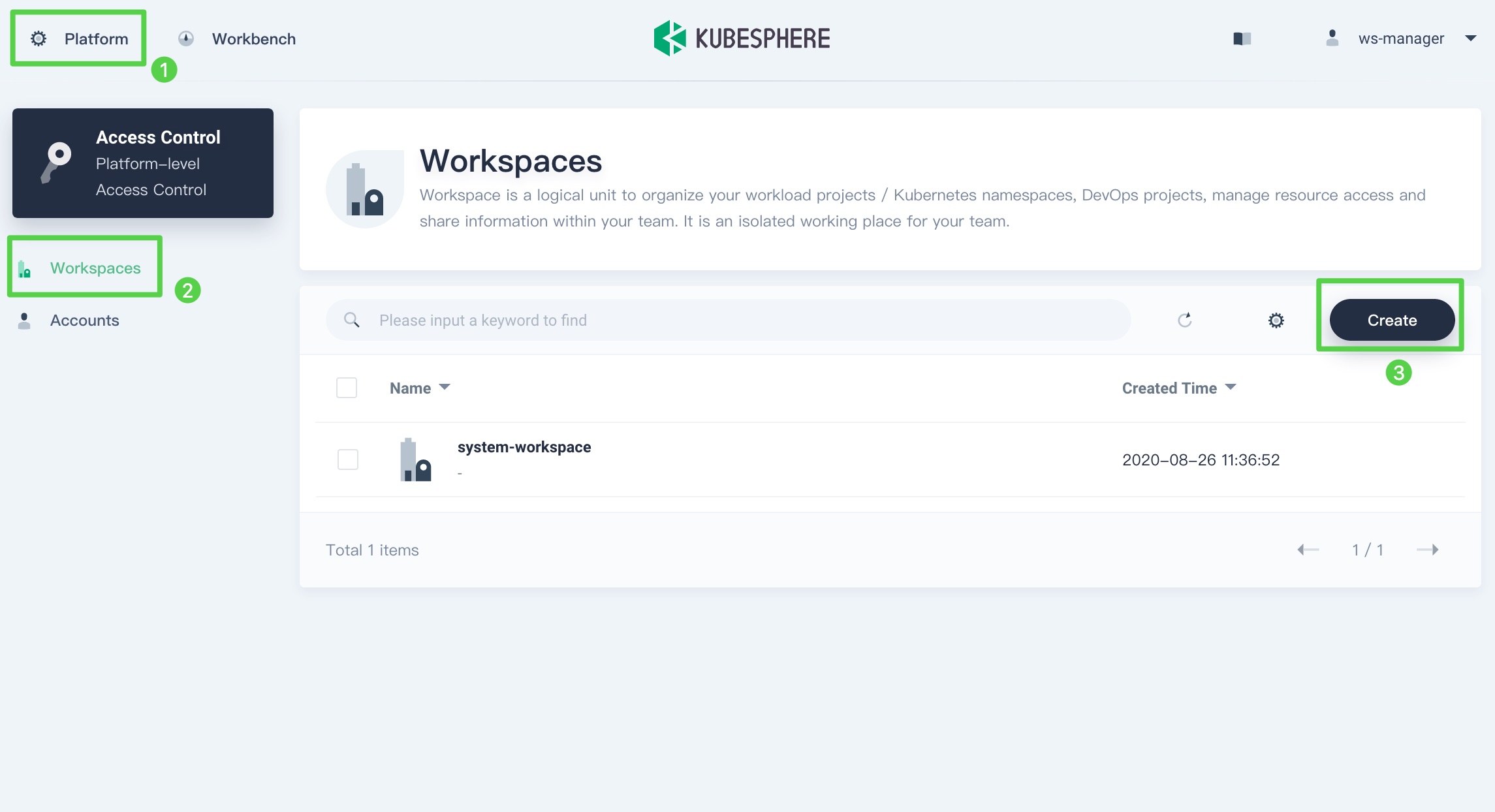
-
Click Create on the right, name the new workspace
demo-workspaceand set the userws-adminas the workspace manager shown in the screenshot below: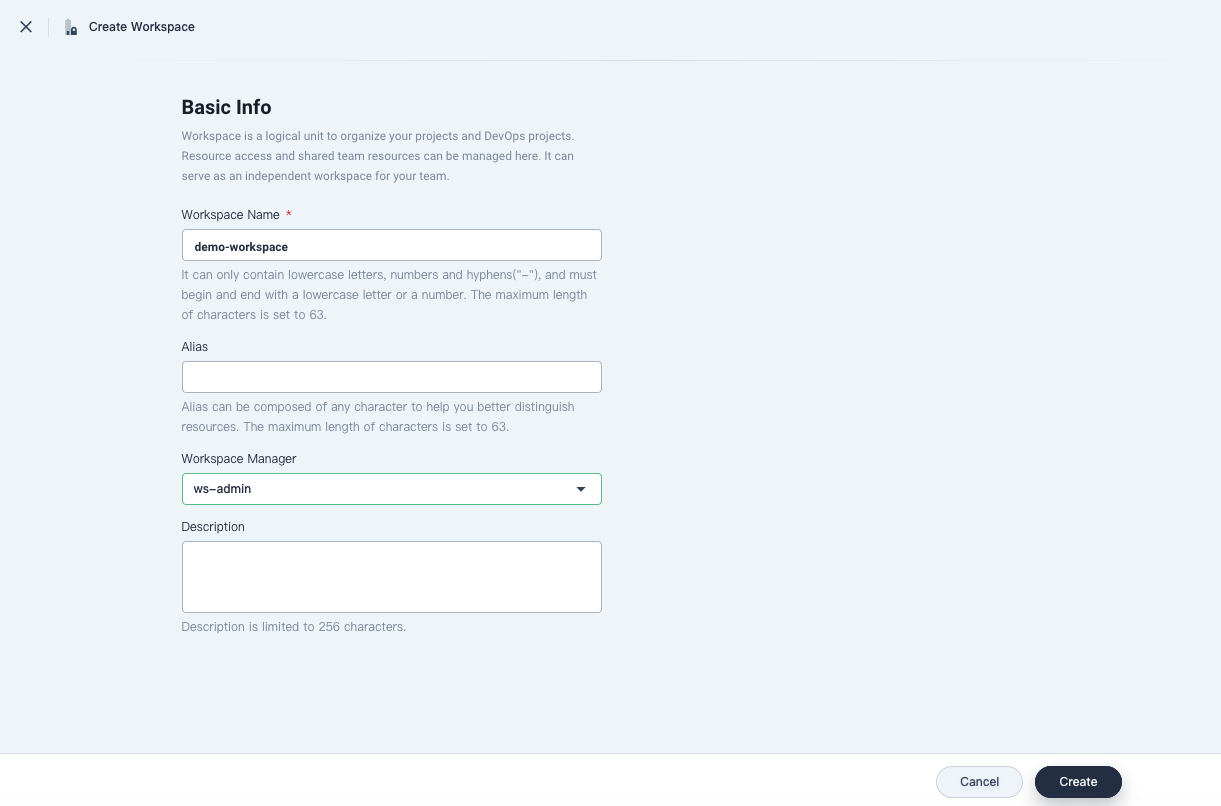
Click Create after you finish.
Note
If you have enabled the multi-cluster feature, you need to assign an available cluster (or multiple clusters) to the workspace so that projects can be created on the cluster(s) later. -
Log out of the console and log back in as
ws-admin. In Workspace Settings, select Workspace Members and click Invite Member.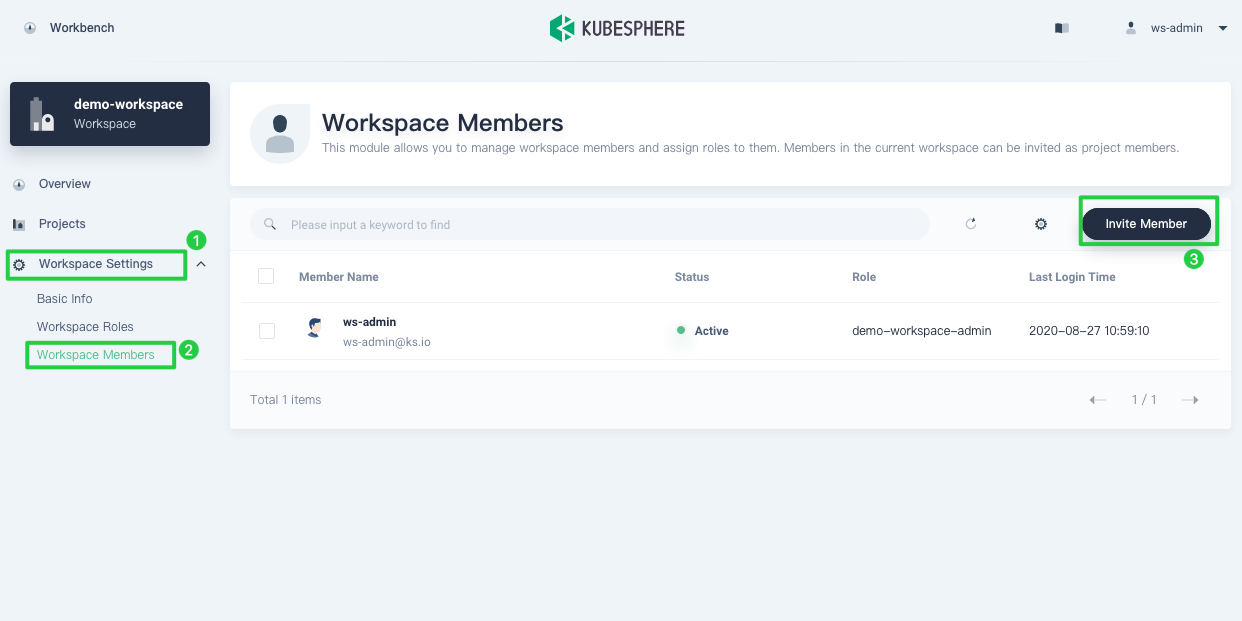
-
Invite both
project-adminandproject-regularto the workspace. Grant them the roleworkspace-self-provisionerandworkspace-viewerrespectively.Note
The actual role name follows a naming convention:<workspace name>-<role name>. For example, in this workspace nameddemo-workspace, the actual role name of the roleviewerisdemo-workspace-viewer.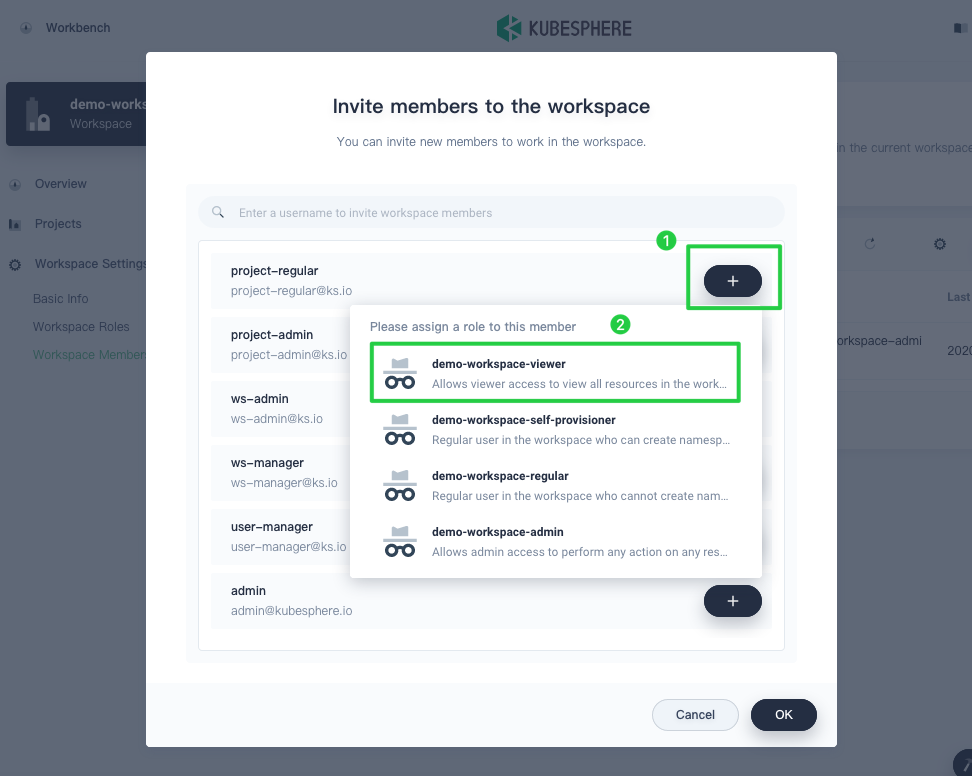
-
After you add both
project-adminandproject-regularto the workspace, click OK. In Workspace Members, you can see three members listed.Account Role Description ws-adminworkspace-adminManage all resources under the workspace (Use this account to invite new members to the workspace). project-adminworkspace-self-provisionerCreate and manage projects and DevOps projects, and invite new members to join the projects. project-regularworkspace-viewerproject-regularwill be invited byproject-adminto join a project or DevOps project. The account can be used to create workloads, pipelines, etc.
Step 3: Create a project
In this step, you create a project using the account project-admin created in the previous step. A project in KubeSphere is the same as a namespace in Kubernetes, which provides virtual isolation for resources. For more information, see Namespaces.
-
Log in to KubeSphere as
project-admin. In Projects, click Create.
-
Enter the project name (for example,
demo-project) and click OK to finish. You can also add an alias and description for the project.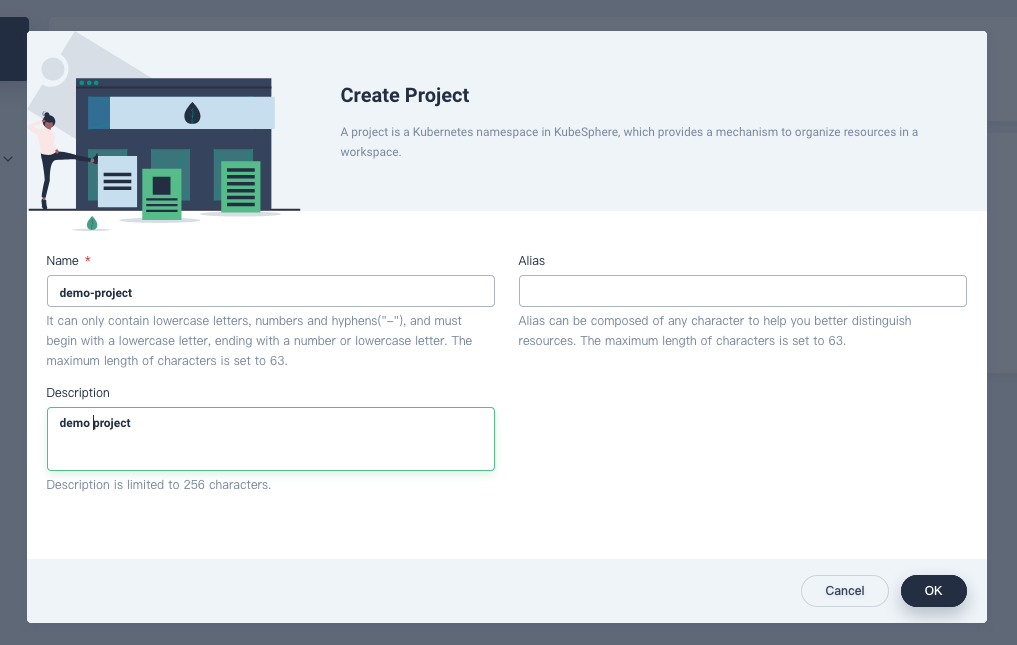
-
In Projects, click the project created just now to view its detailed information.
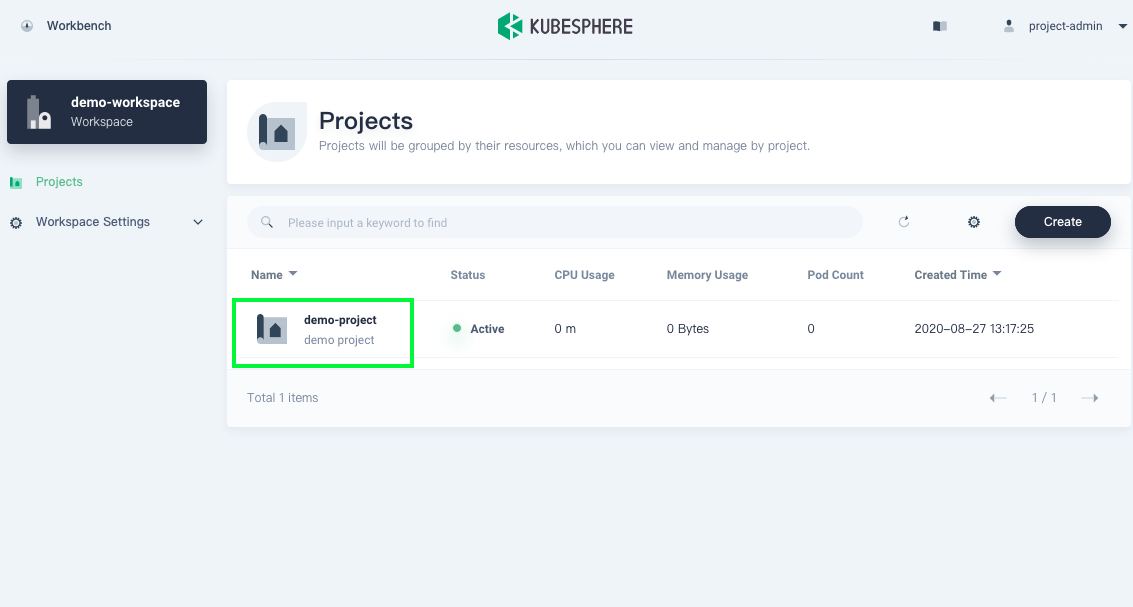
-
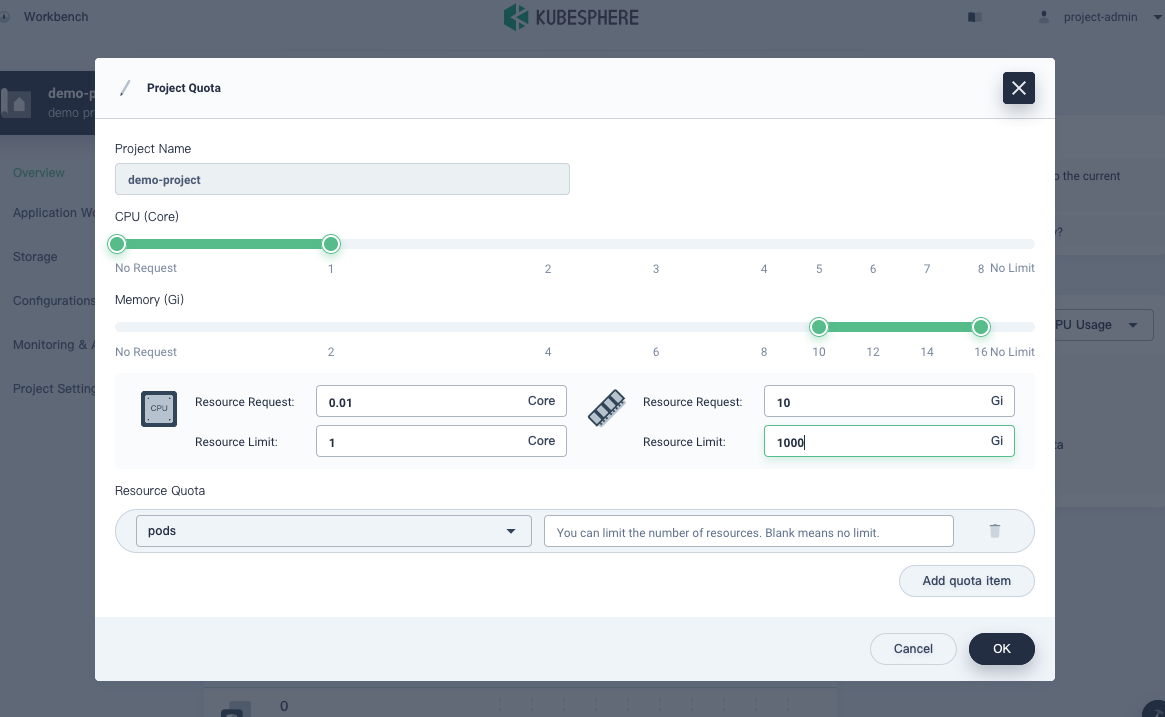
On the Overview page of the project, the project quota remains unset by default. You can click Set and specify resource requests and limits as needed (for example, 1 core for CPU and 1000Gi for memory).
-
Invite
project-regularto this project and grant this user the roleoperator. Refer to the image below for specific steps.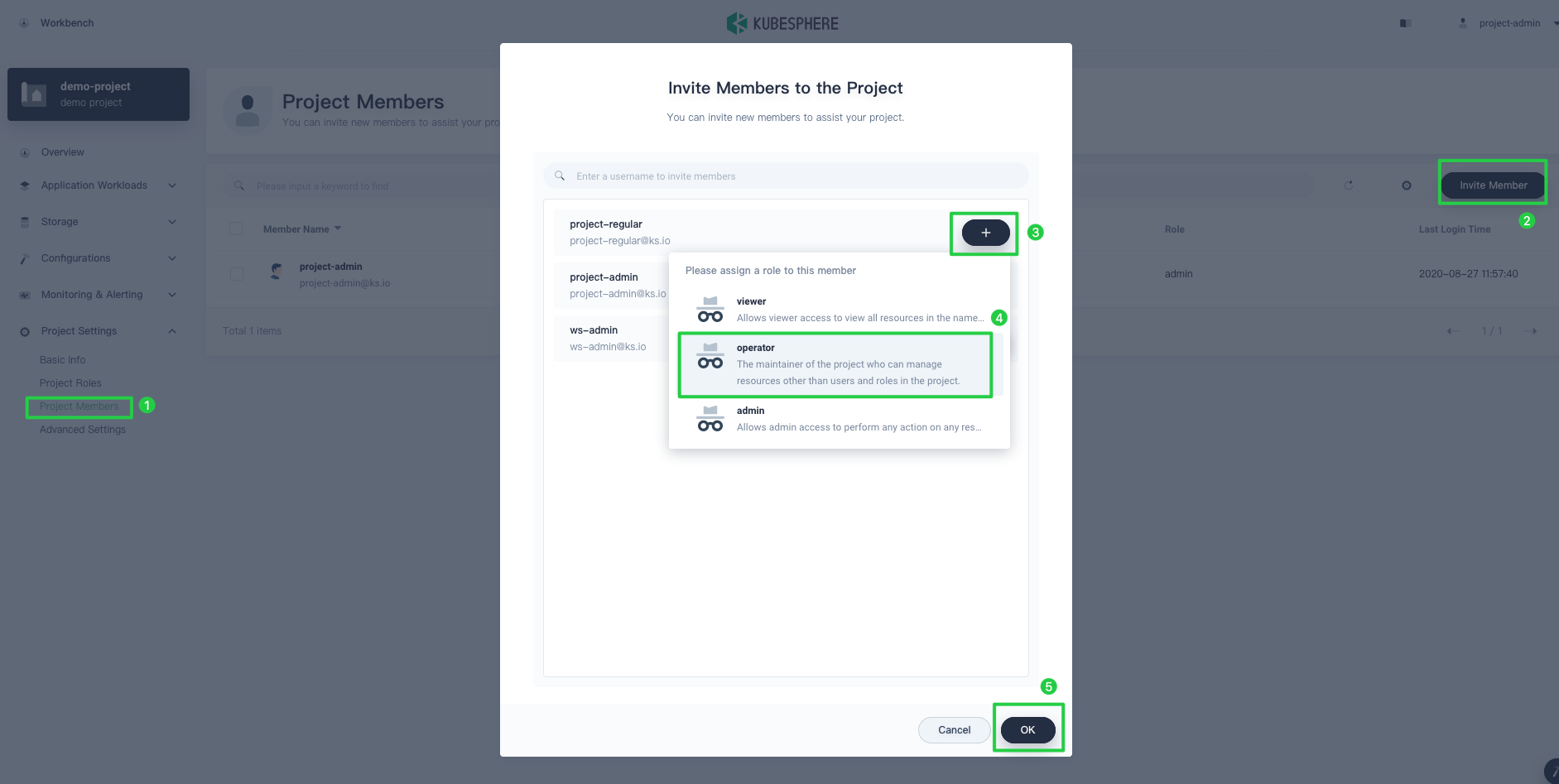
Info
The user granted the roleoperatorwill be a project maintainer who can manage resources other than users and roles in the project. -
Before creating a Route which is Ingress in Kubernetes, you need to enable a gateway for this project. The gateway is an NGINX Ingress controller running in the project. To set a gateway, go to Advanced Settings in Project Settings and click Set Gateway. The account
project-adminis still used in this step.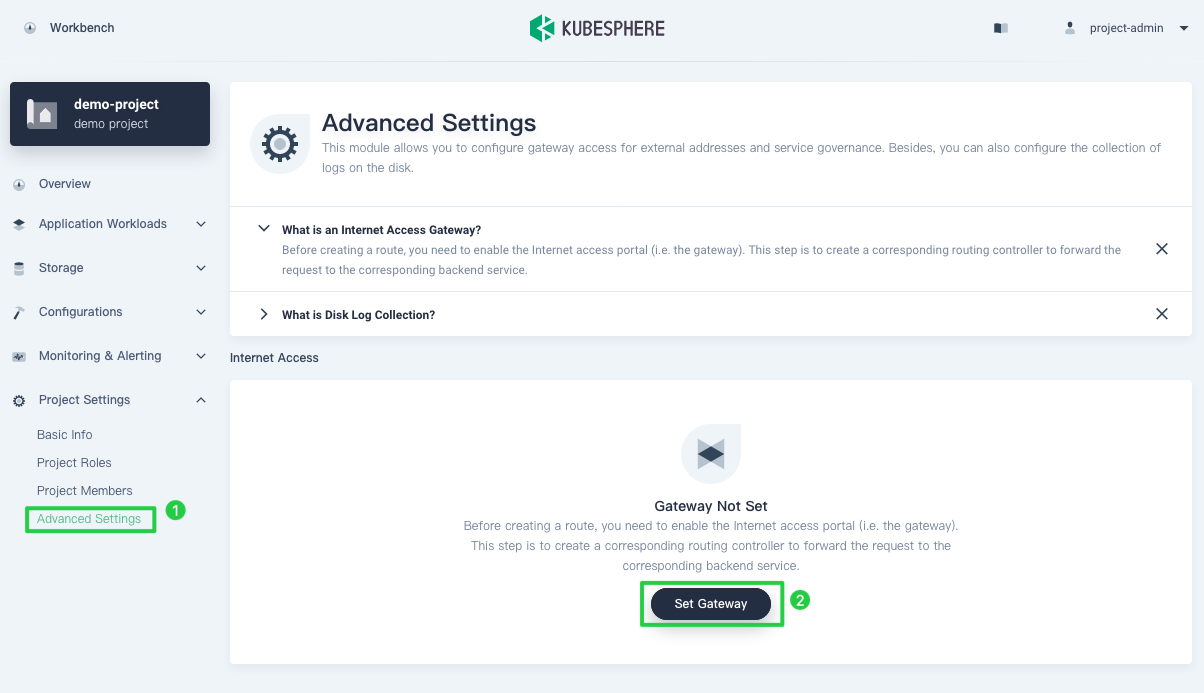
-
Choose the access method NodePort and click Save.
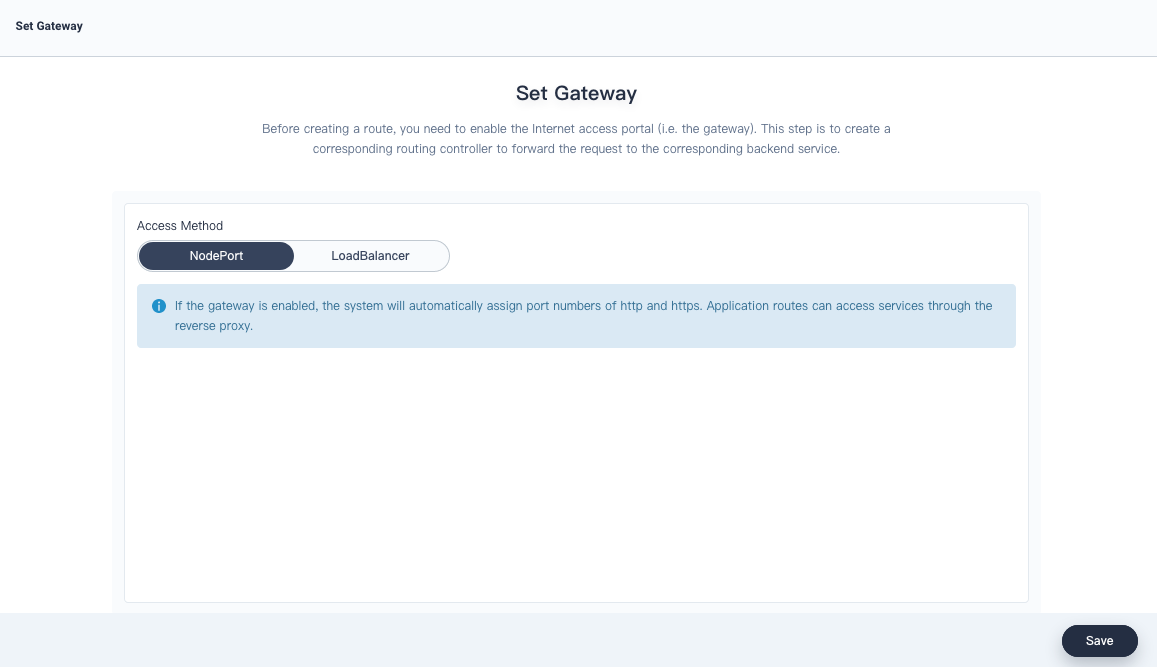
-
Under Internet Access, it can be seen that the Gateway Address and the NodePort of http and https all display on the page.
Note
If you want to expose services using the typeLoadBalancer, you need to use the LoadBalancer plugin of cloud providers. If your Kubernetes cluster is running in a bare metal environment, it is recommended that you use PorterLB as the LoadBalancer plugin.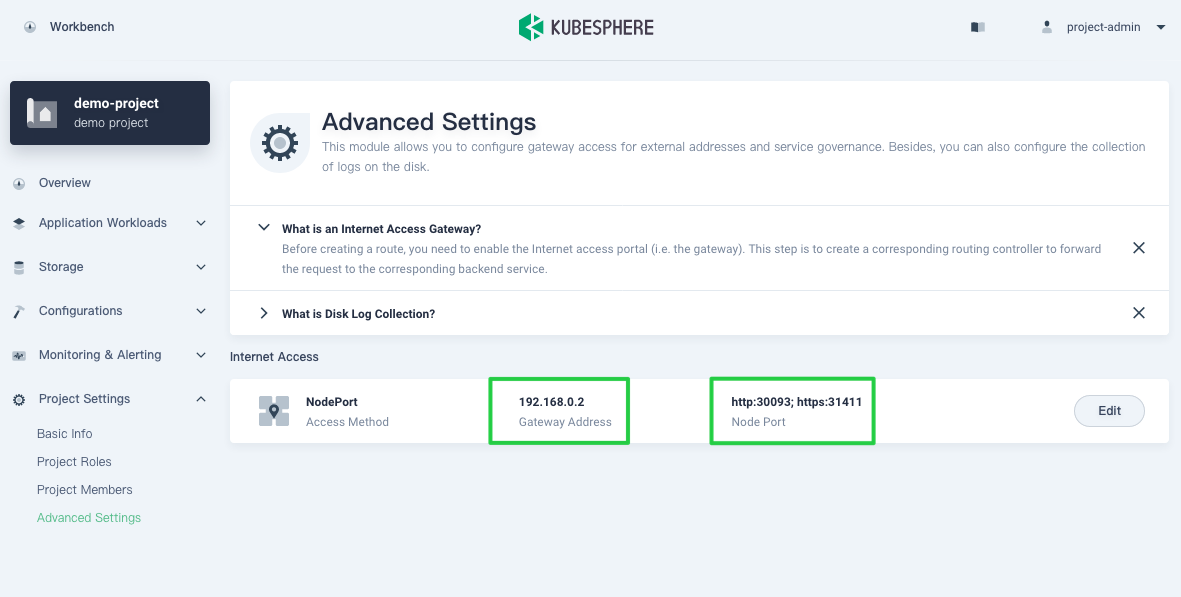
Step 4: Create a role
After you finish the above steps, you know that users can be granted different roles at different levels. The roles used in previous steps are all built-in ones created by KubeSphere itself. In this step, you will learn how to define a customized role to meet the needs in your work.
-
Log in to the console as
adminagain and go to Access Control. -
In Account Roles, there are four system roles listed which cannot be deleted or edited. Click Create and set a Role Identifier. In this example, a role named
roles-managerwill be created.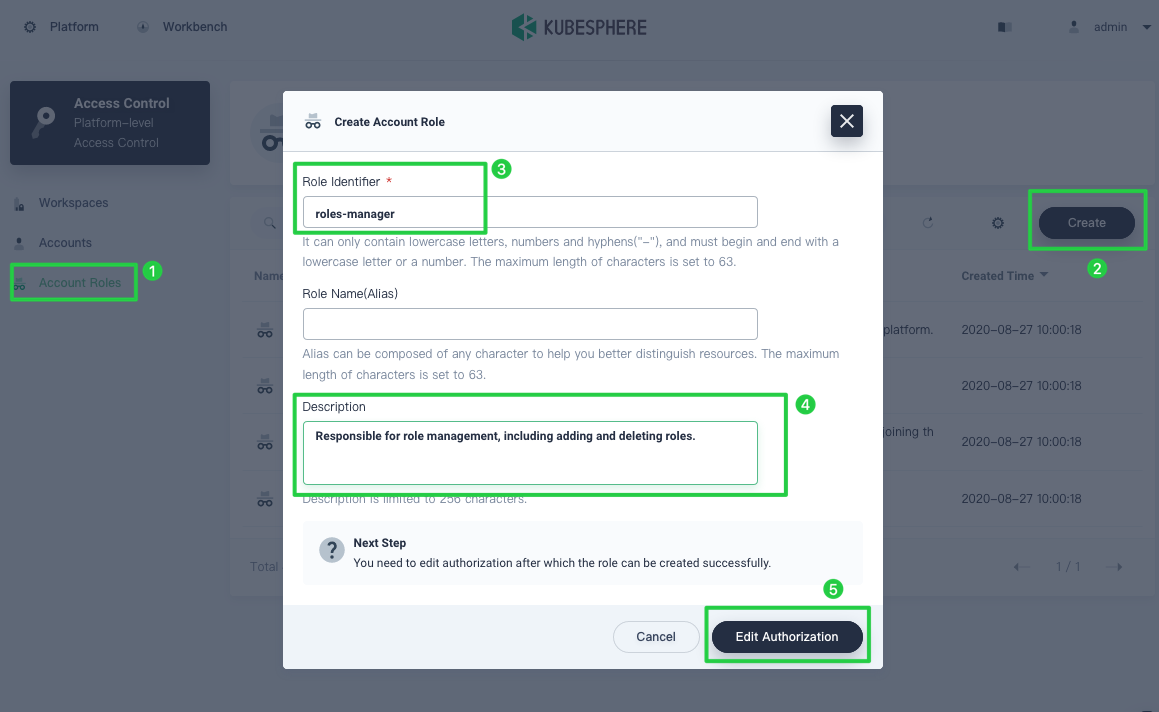
Note
It is recommended you enter a description for the role as it explains what the role is used for. The role created here will be responsible for role management only, including adding and deleting roles.Click Edit Authorization to continue.
-
In Access Control, select the authorization that you want this role to contain. For example, Users View, Roles Management and Roles View are selected for this role. Click OK to finish.
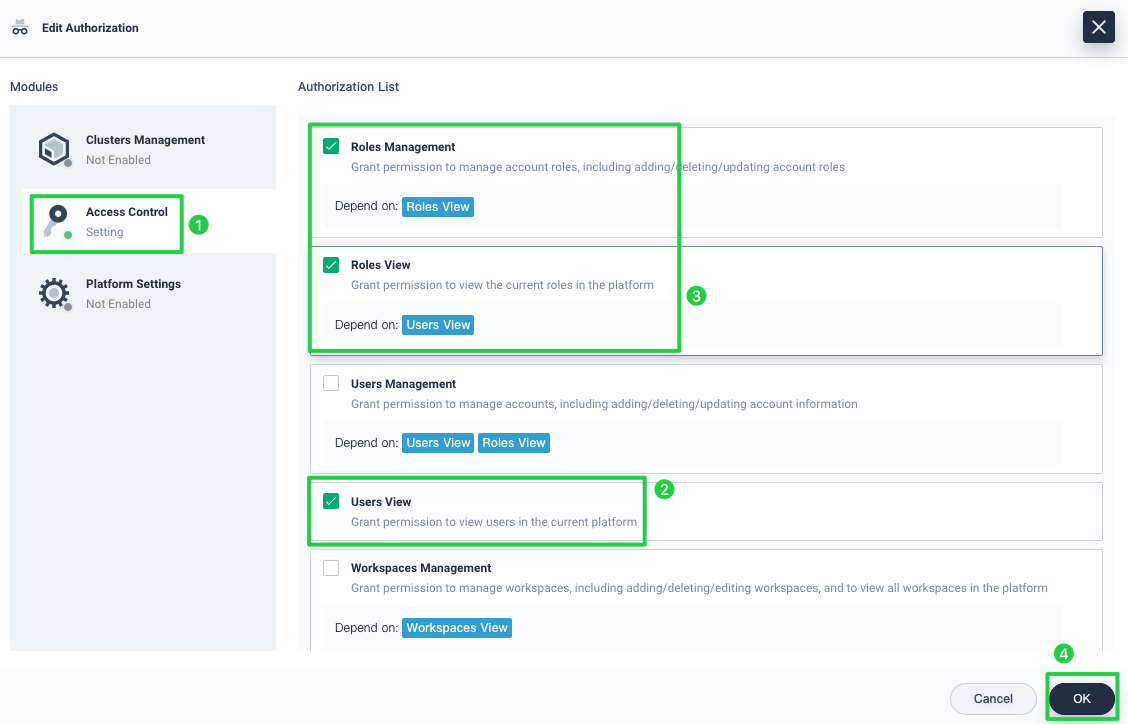
Note
Depend on means the major authorization (the one listed after Depend on) needs to be selected first so that the affiliated authorization can be assigned. -
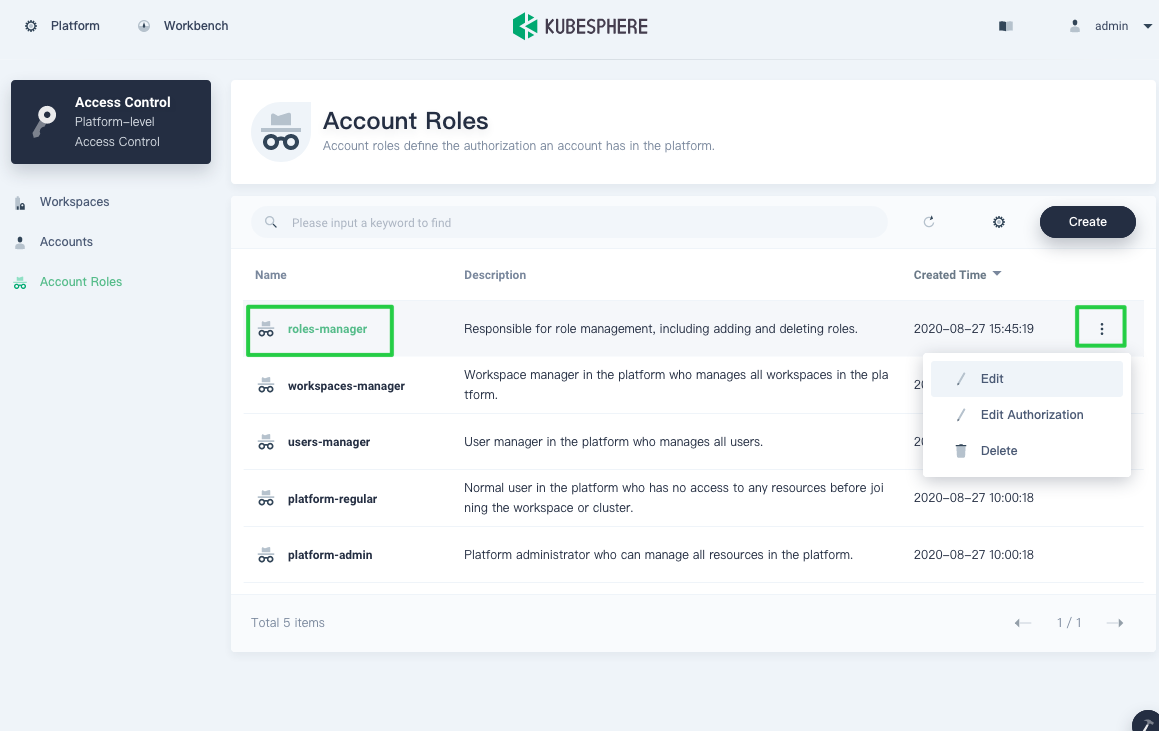
Newly-created roles will be listed in Account Roles. You can click the three dots on the right to edit it.
-
In Accounts, you can add a new account and grant it the role
roles-manageror change the role of an existing account toroles-managerby editing it.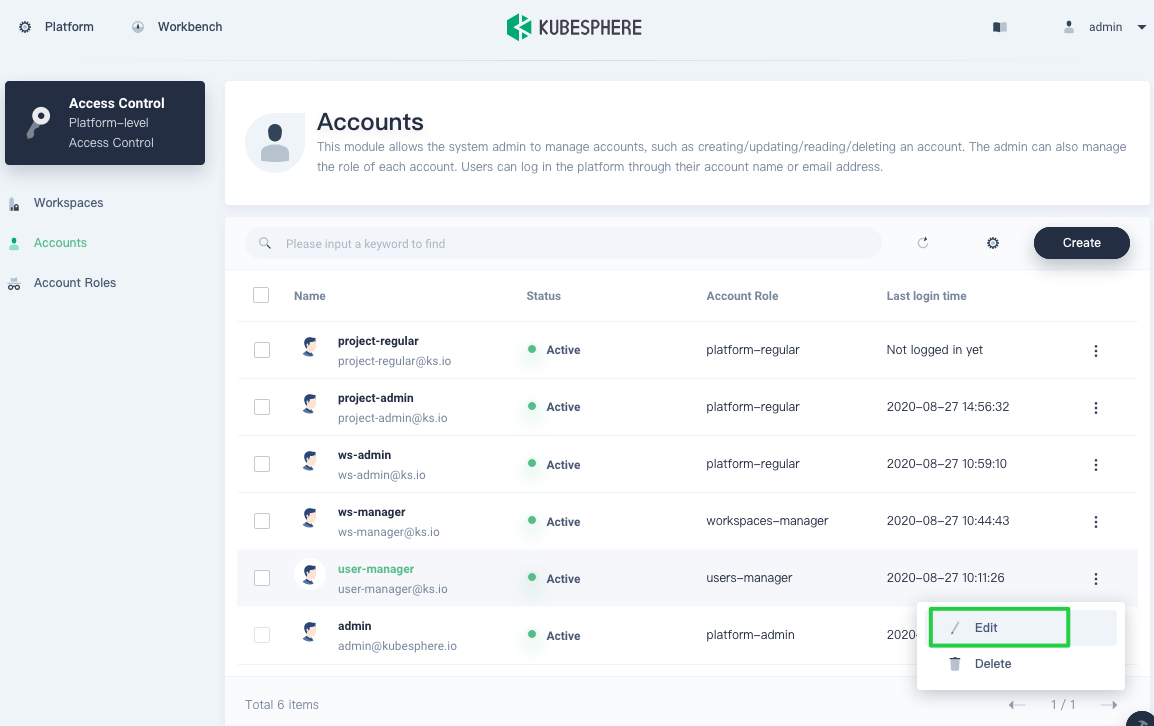
Note
The role ofroles-manageroverlaps withusers-managerwhile the latter is also capable of user management. This example is only for demonstration purposes. You can create customized roles based on your needs.
Step 5: Create a DevOps project (Optional)
Note
-
Log in to the console as
project-admin. In DevOps Projects, click Create.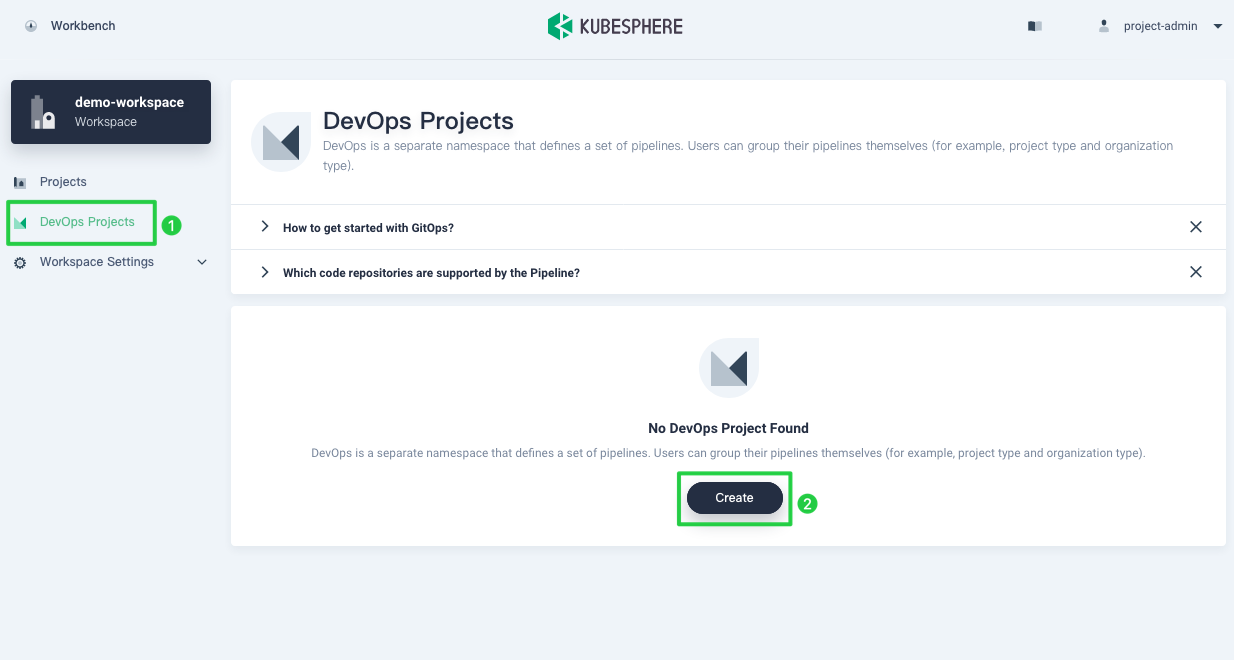
-
Enter the DevOps project name (for example,
demo-devops) and click OK. You can also add an alias and description for the project.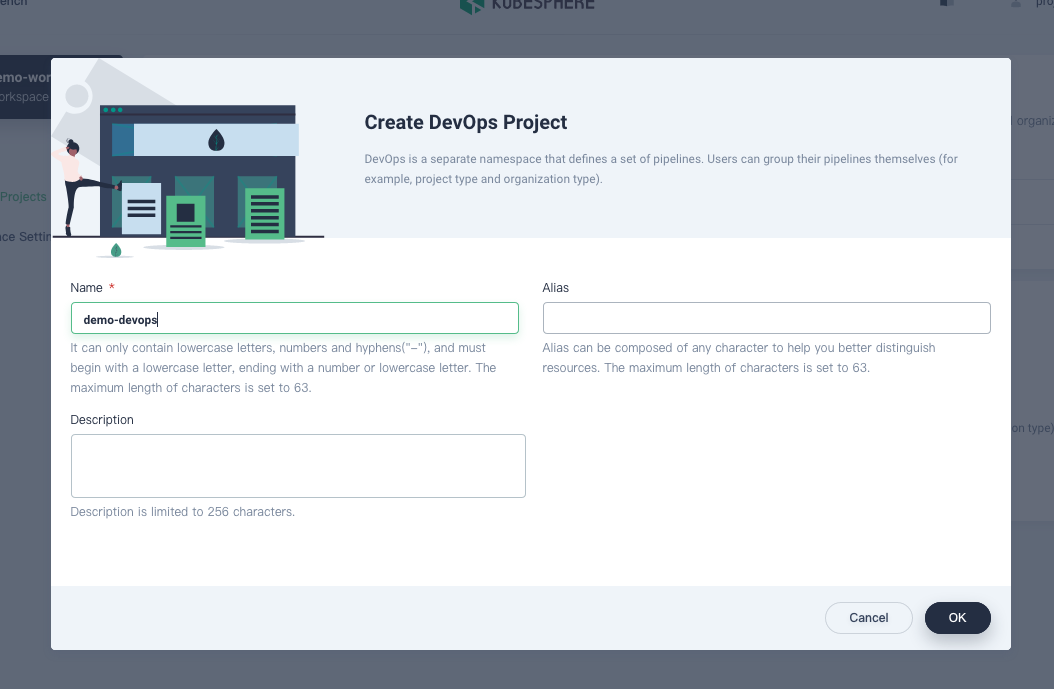
-
In DevOps Projects, click the project created just now to view its detailed information.
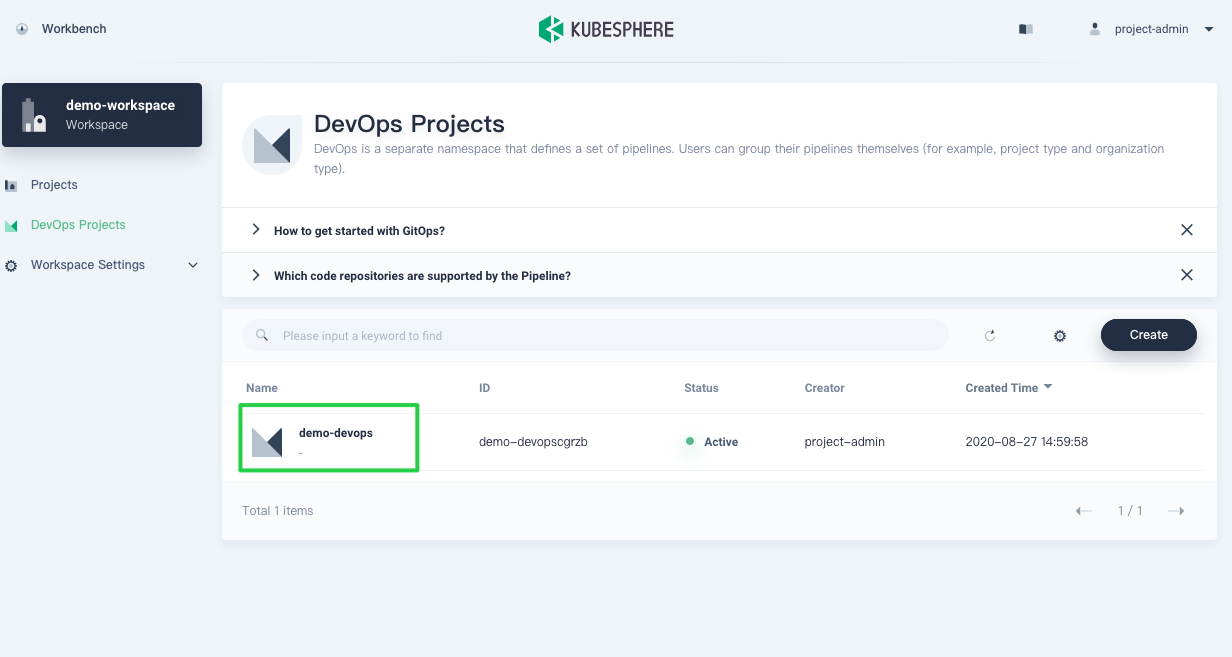
-
Go to Project Management and select Project Members. Click Invite Member to grant
project-regularthe role ofoperator, who is allowed to create pipelines and credentials.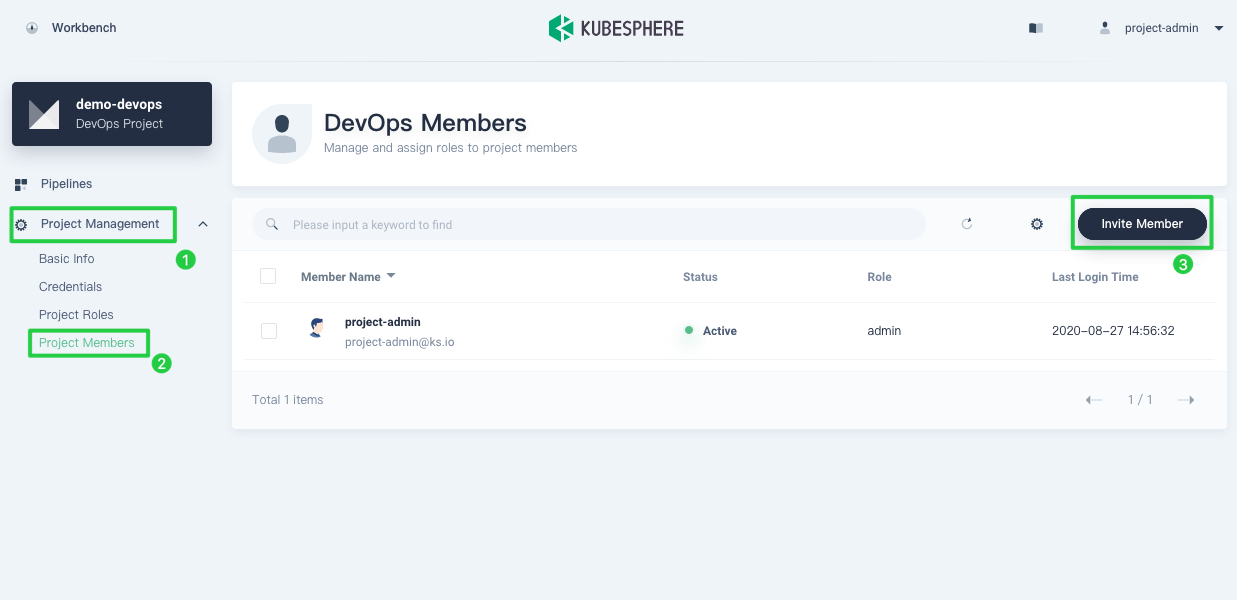
You are now familiar with the multi-tenant management system of KubeSphere. In other tutorials, the account project-regular will also be used to demonstrate how to create applications and resources in a project or DevOps project.













 Previous
Previous
