
You are viewing documentation for KubeSphere version:v3.0.0
KubeSphere v3.0.0 documentation is no longer actively maintained. The version you are currently viewing is a static snapshot. For up-to-date documentation, see the latest version.
Deploy Harbor on KubeSphere
Harbor is an open-source registry that secures artifacts with policies and role-based access control, ensures images are scanned and free from vulnerabilities, and signs images as trusted.
This tutorial walks you through an example of deploying Harbor from the App Store of KubeSphere.
Prerequisites
- Please make sure you enable the OpenPitrix system.
- You need to create a workspace, a project, and a user account for this tutorial. The account needs to be a platform regular user and to be invited as the project operator with the
operatorrole. In this tutorial, you log in asproject-regularand work in the projectdemo-projectin the workspacedemo-workspace. For more information, see Create Workspaces, Projects, Accounts and Roles.
Hands-on Lab
Step 1: Deploy Harbor from the App Store
-
On the Overview page of the project
demo-project, click App Store in the top left corner.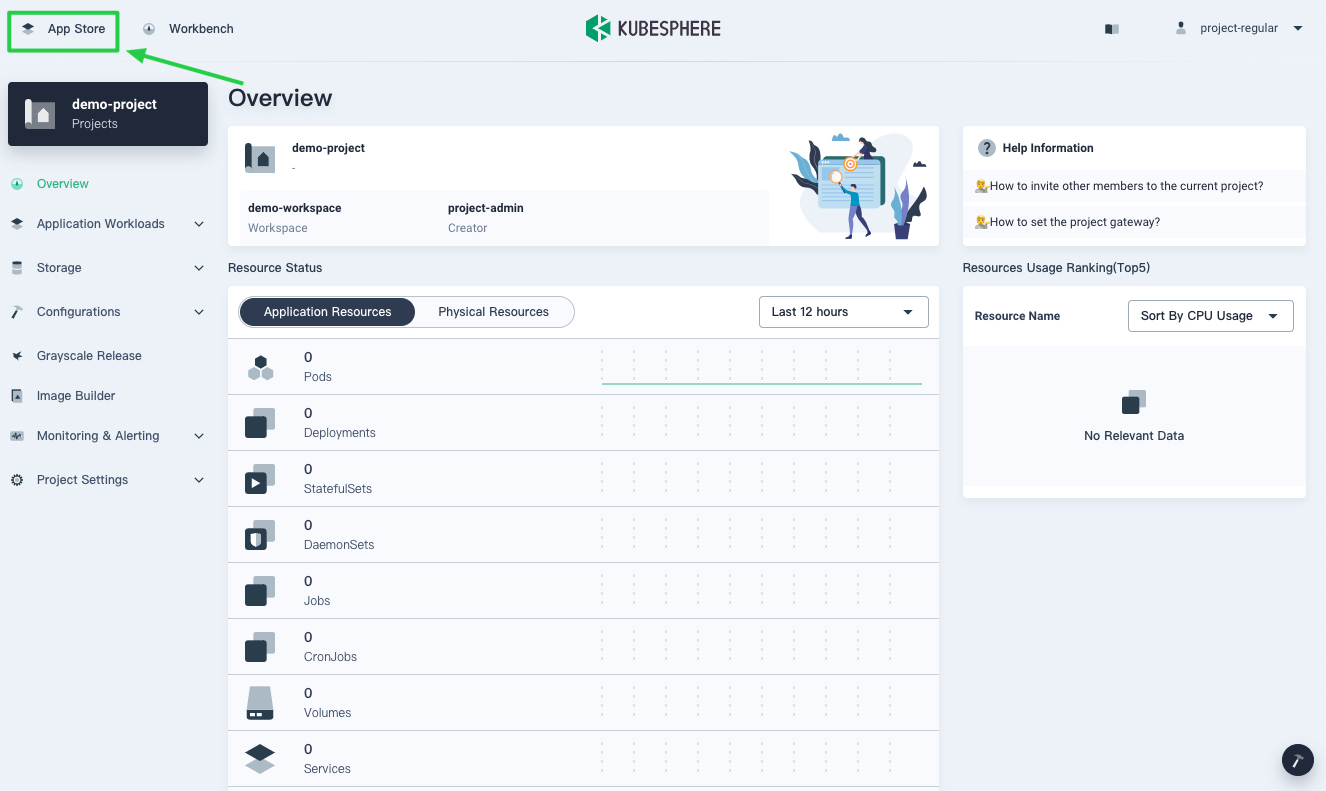
-
Find Harbor and click Deploy on the App Info page.
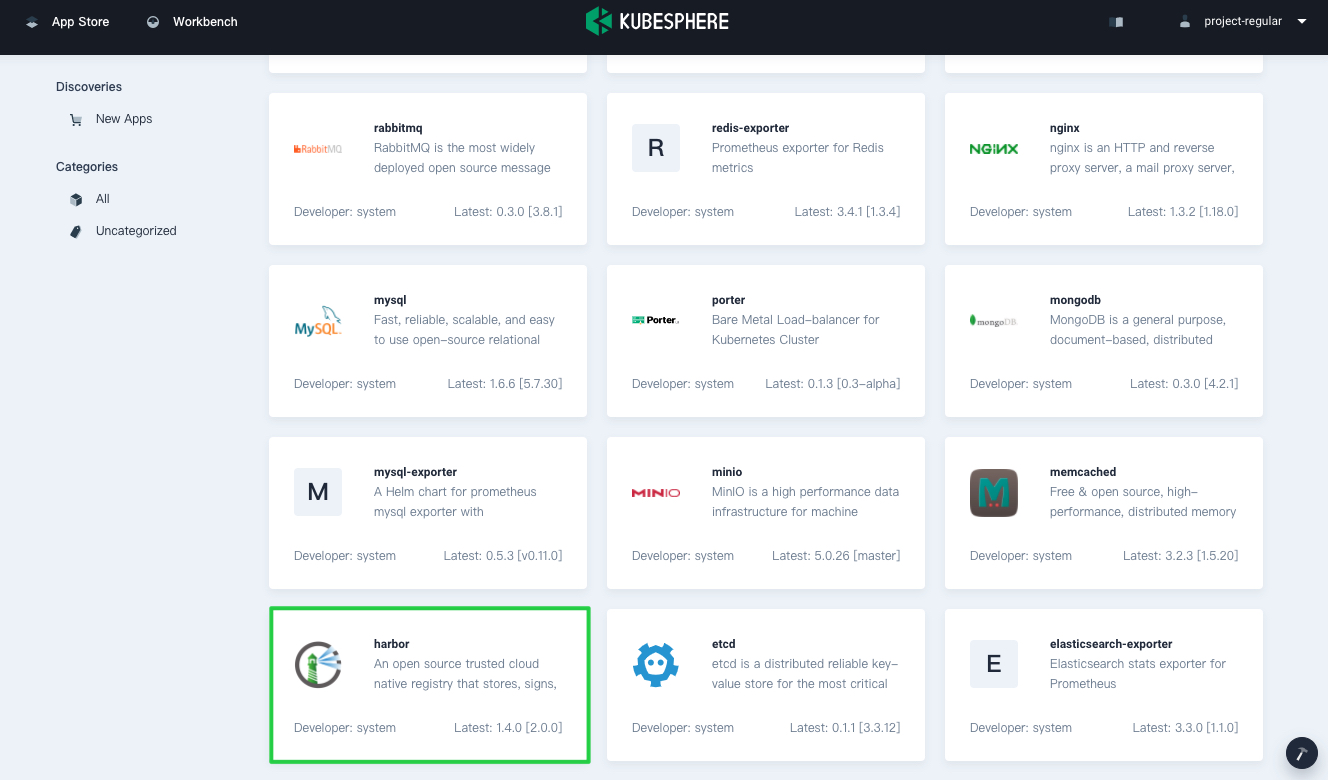
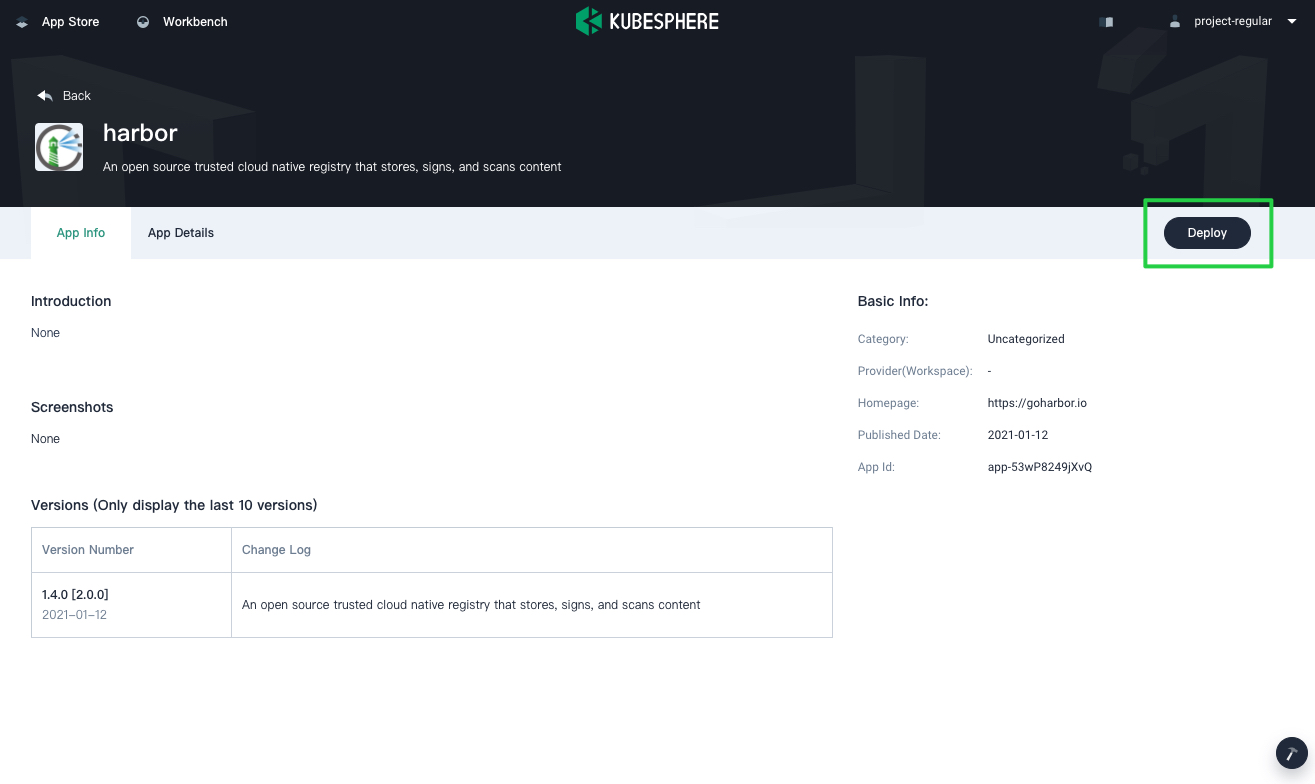
-
Set a name and select an app version. Make sure Harbor is deployed in
demo-projectand click Next.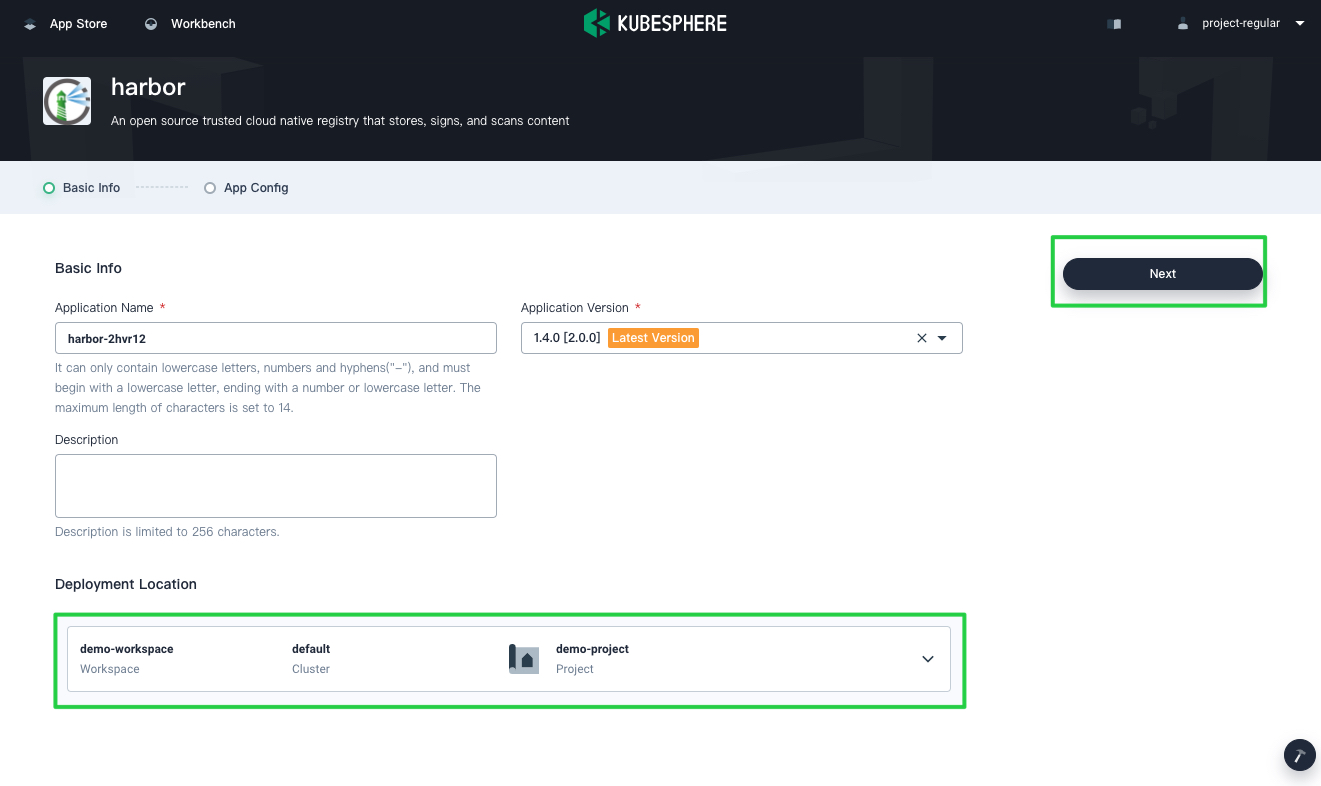
-
On the App Config page, edit the configuration file of Harbor. Pay attention to the following fields.
type: The method you use to access the Harbor Service. This example usesnodePort.tls: Specify whether you want to enable HTTPS. Set it tofalsefor most cases.externalURL: The URL exposed to tenants.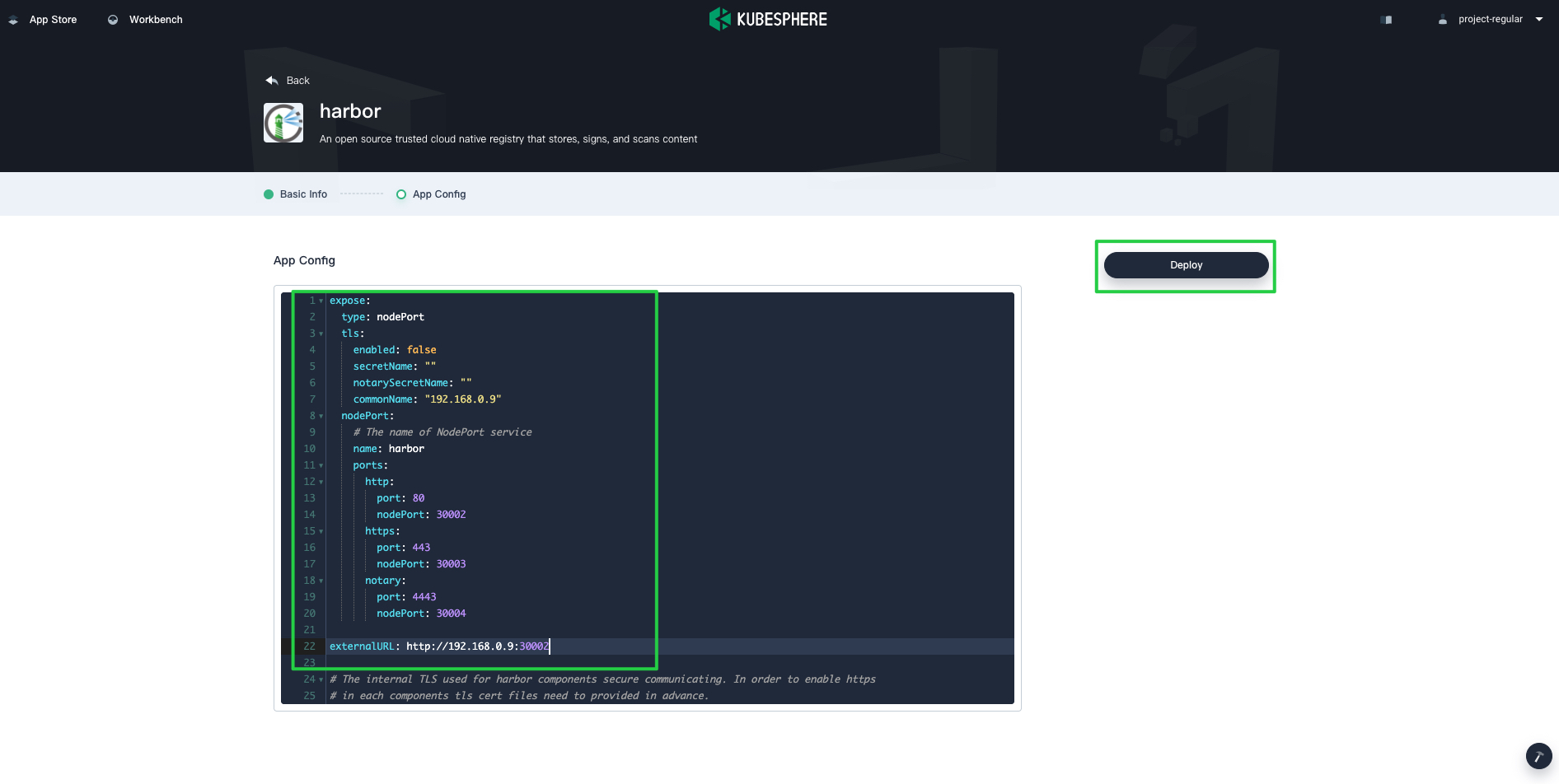
Note
-
Don’t forget to specify
externalURL. This field can be very helpful if you have trouble accessing Harbor. -
Make sure you use the HTTP protocol and its corresponding
nodePortin this tutorial. For more information, see the example configuration in FAQ.
When you finish editing the configuration, click Deploy to continue.
-
-
Wait until Harbor is up and running.
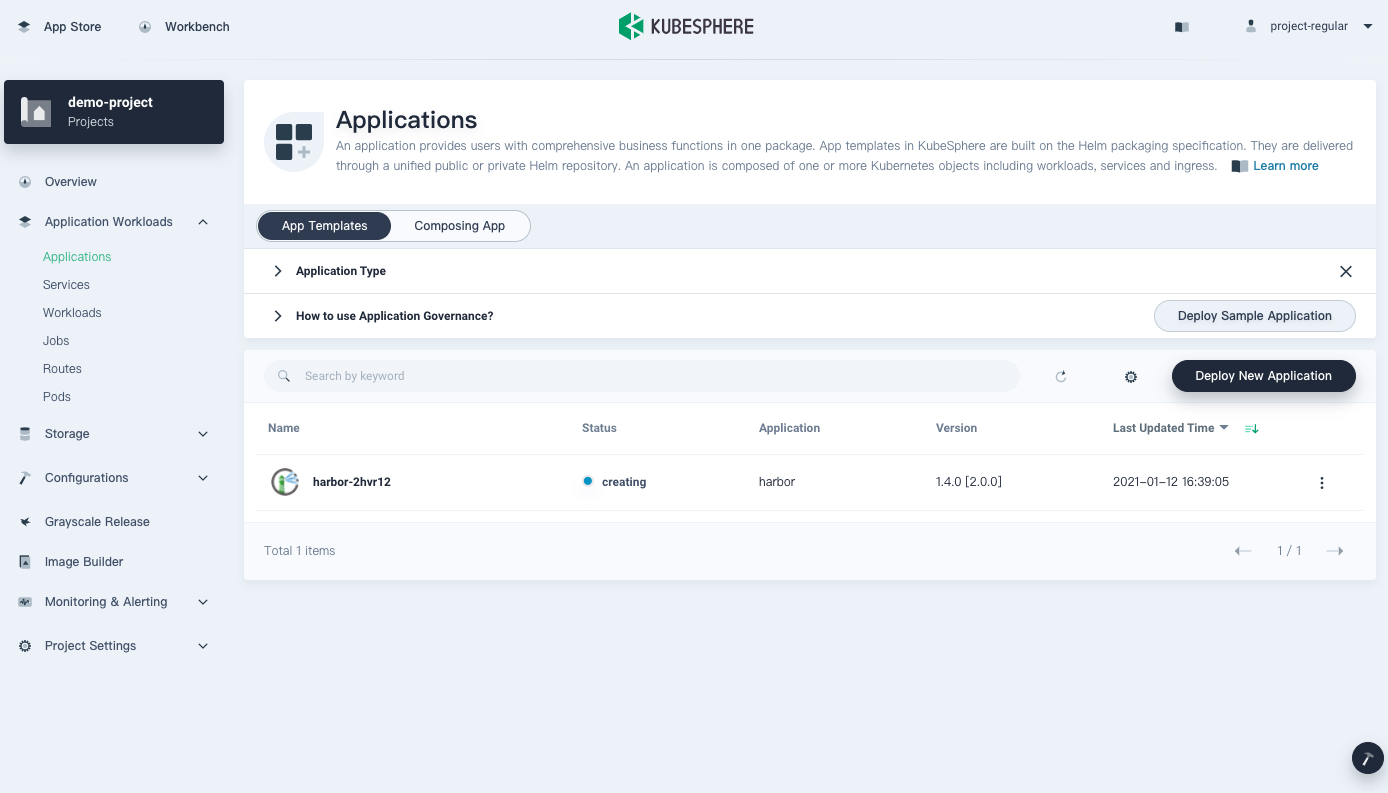
Step 2: Access Harbor
-
Based on the field
expose.typeyou set in the configuration file, the access method may be different. As this example usesnodePortto access Harbor, visithttp://nodeIP:30002as set in the previous step.
Note
You may need to open the port in your security groups and configure related port forwarding rules depending on your where your Kubernetes cluster is deployed. -
Log in to Harbor using the default account and password (
admin/Harbor12345). The password is defined in the fieldharborAdminPasswordin the configuration file.
FAQ
-
How to enable HTTP login?
Set
tls.enabledtofalsein step 1 above. The protocol ofexternalURLmust be the same asexpose.type.ports.If you use Docker login, set
externalURLto one ofinsecure-registriesindaemon.json, then reload Docker.Here is an example configuration file for your reference. Pay special attention to the comments.
## NOTICE 192.168.0.9 is the example IP address and you must use your own. expose: type: nodePort tls: enabled: false secretName: "" notarySecretName: "" commonName: "192.168.0.9" # Change commonName to your own. nodePort: # The name of NodePort service name: harbor ports: http: # The service port Harbor listens on when serving with HTTP port: 80 # The node port Harbor listens on when serving with HTTP nodePort: 30002 https: # The service port Harbor listens on when serving with HTTPS port: 443 # The node port Harbor listens on when serving with HTTPS nodePort: 30003 # Only needed when notary.enabled is set to true notary: # The service port Notary listens on port: 4443 # The node port Notary listens on nodePort: 30004 externalURL: http://192.168.0.9:30002 # Use your own IP address. # The initial password of Harbor admin. Change it from portal after launching Harbor harborAdminPassword: "Harbor12345" # The secret key used for encryption. Must be a string of 16 chars. secretKey: "not-a-secure-key" -
How to enable HTTPS login?
a. Use self-signed certificates.
- Set
tls.enabledtotruein the configuration file in step 1, and editexternalURLaccordingly. - Copy the CA certificates stored in the Pod
harbor-core's/etc/core/cato your host. - Trust the CA certificates by your host first, then restart Docker.
b. Use public SSL.
- Add certificates as a Secret.
- Set
tls.enabledtotruein the configuration file in step 1, and editexternalURLaccordingly. - Edit
tls.secretName.
- Set
For more information, see the documentation of Harbor.













 Previous
Previous
