
You are viewing documentation for KubeSphere version:v3.0.0
KubeSphere v3.0.0 documentation is no longer actively maintained. The version you are currently viewing is a static snapshot. For up-to-date documentation, see the latest version.
Integrate Harbor into Pipelines
This tutorial demonstrates how to integrate Harbor into KubeSphere pipelines.
Prerequisites
- You need to enable the KubeSphere DevOps System.
- You need to create a workspace, a DevOps project, and an account (
project-regular). This account needs to be invited to the DevOps project with theoperatorrole. See Create Workspaces, Projects, Accounts and Roles if they are not ready.
Install Harbor
It is highly recommended that you install Harbor through the App Store of KubeSphere. Alternatively, install Harbor manually through Helm3.
helm repo add harbor https://helm.goharbor.io
# For a quick start, you can expose Harbor by nodeport and disable tls.
# Set externalURL to one of your node ip and make sure it can be accessed by jenkins.
helm install harbor-release harbor/harbor --set expose.type=nodePort,externalURL=http://$ip:30002,expose.tls.enabled=false
Get Harbor Credentials
-
After Harbor is installed, visit
NodeIP:30002and log in to the console with the default account and password (admin/Harbor12345). Go to Projects and click NEW PROJECT.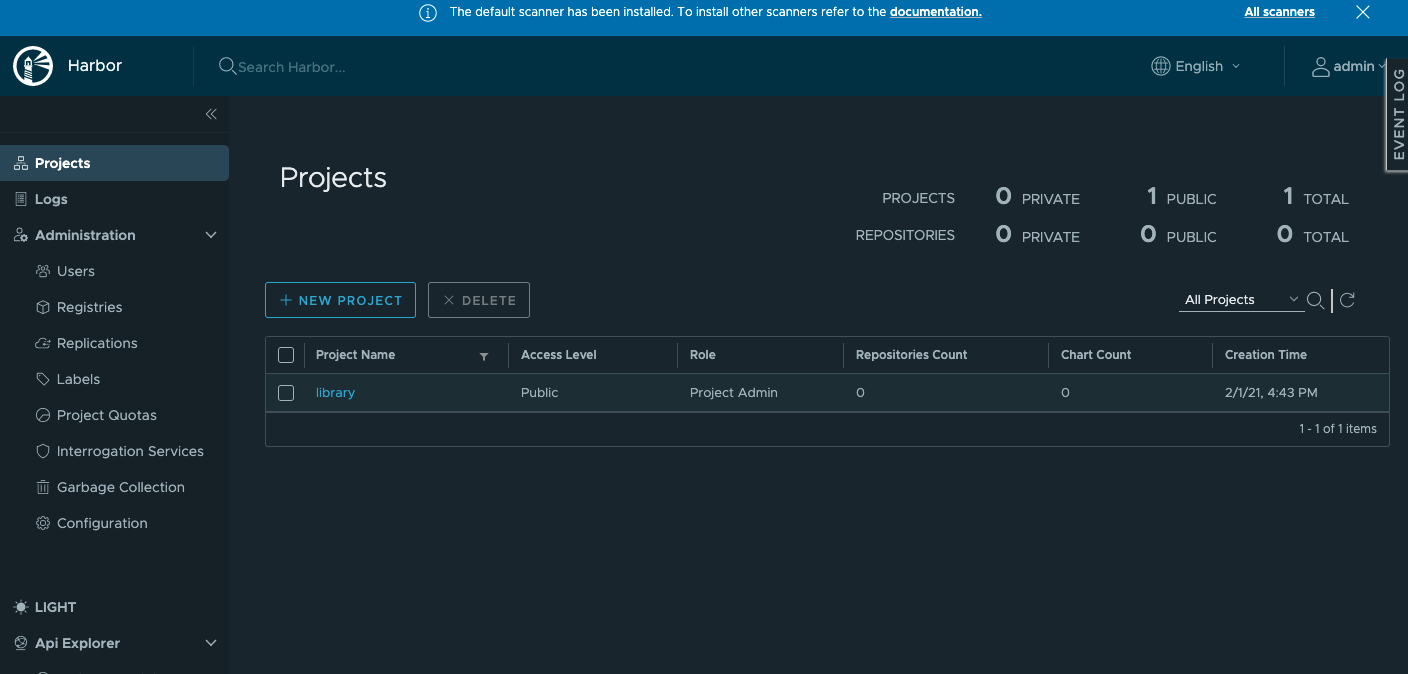
-
Set a name (
ks-devops-harbor) and click OK.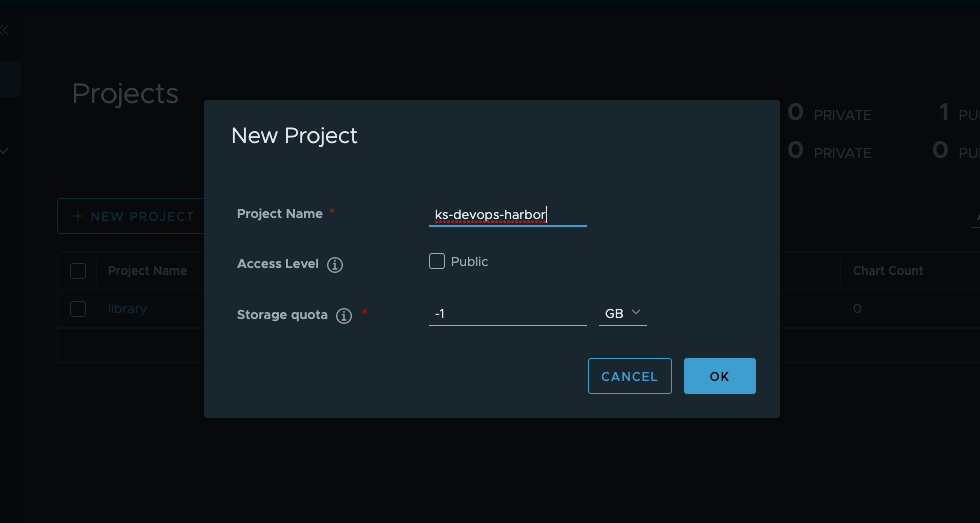
-
Click the project you just created, and select NEW ROBOT ACCOUNT in Robot Accounts.
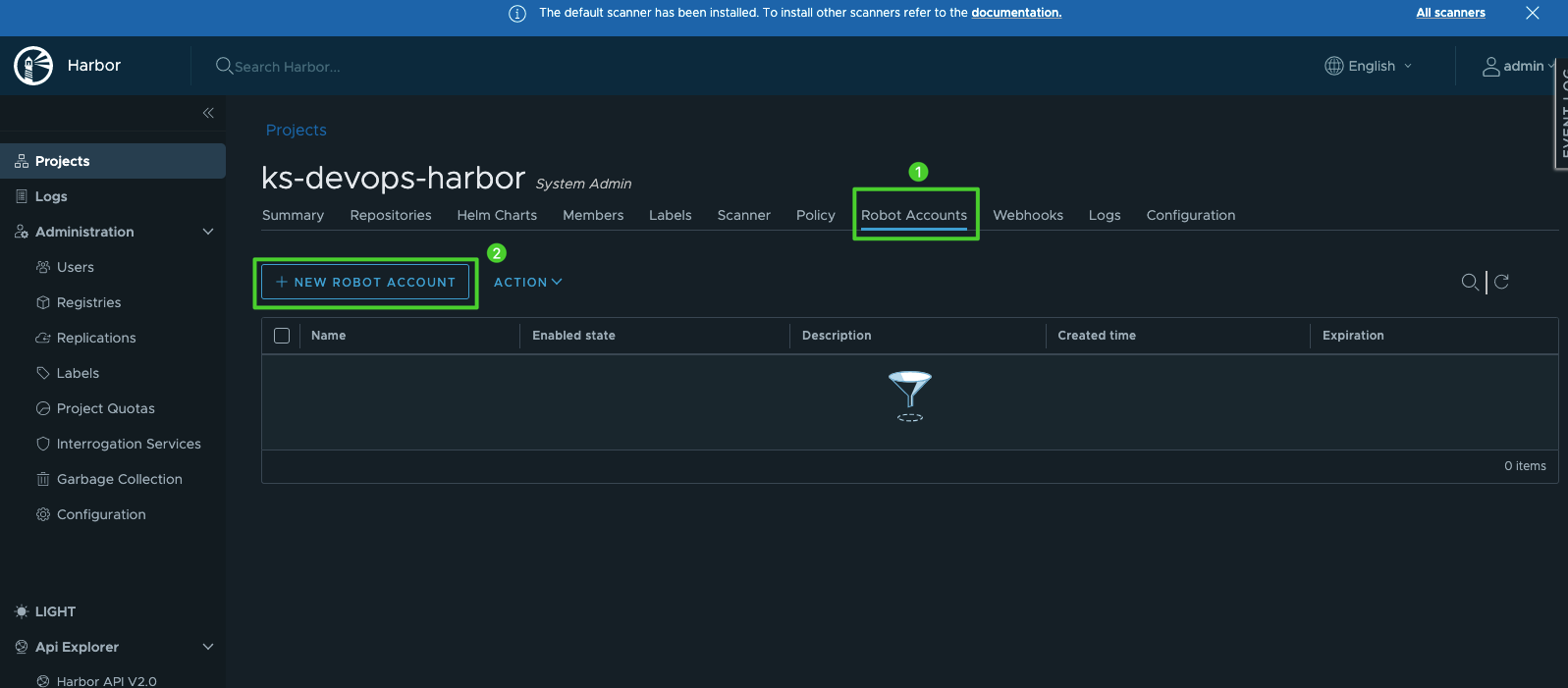
-
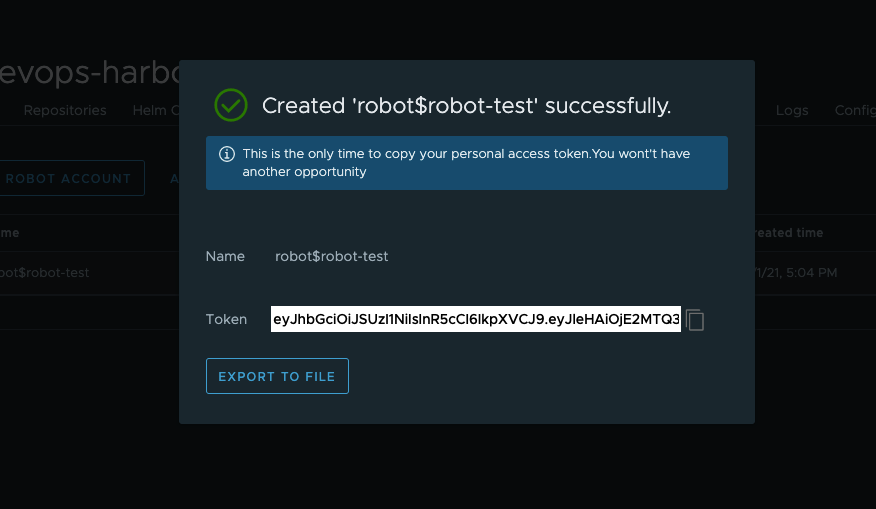
Set a name (
robot-test) for the robot account and save it.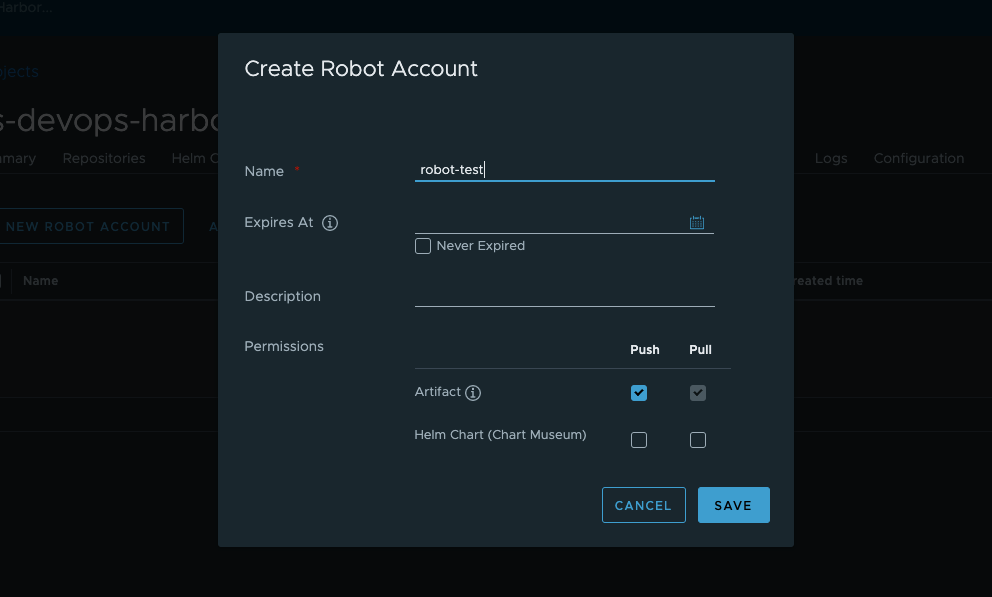
-
Click EXPORT TO FILE to save the token.
Enable Insecure Registry
You have to configure Docker to disregard security for your Harbor registry.
-
Run the
vim /etc/docker/daemon.jsoncommand on your host to edit thedaemon.jsonfile, enter the following contents, and save the changes.{ "insecure-registries" : ["103.61.38.55:30002"] }Note
Make sure you replace103.61.38.55:30002with your Harbor registry address. The default location of thedaemon.jsonfile is/etc/docker/daemon.jsonon Linux orC:\ProgramData\docker\config\daemon.jsonon Windows. -
Run the following commands to restart Docker for the changes to take effect.
sudo systemctl daemon-reload sudo systemctl restart dockerNote
It is suggested that you use this solution for isolated testing or in a tightly controlled, air-gapped environment. For more information, refer to Deploy a plain HTTP registry. After you finish the above operations, you can also use the images in your Harbor registry when deploying workloads in your project. You need to create an image Secret for your Harbor registry, and then select your Harbor registry and enter the absolute path of your images in Container Settings under the Container Image tab to search for your images.
Create Credentials
-
Log in to KubeSphere as
project-regular, go to your DevOps project and create credentials for Harbor in Credentials under Project Management.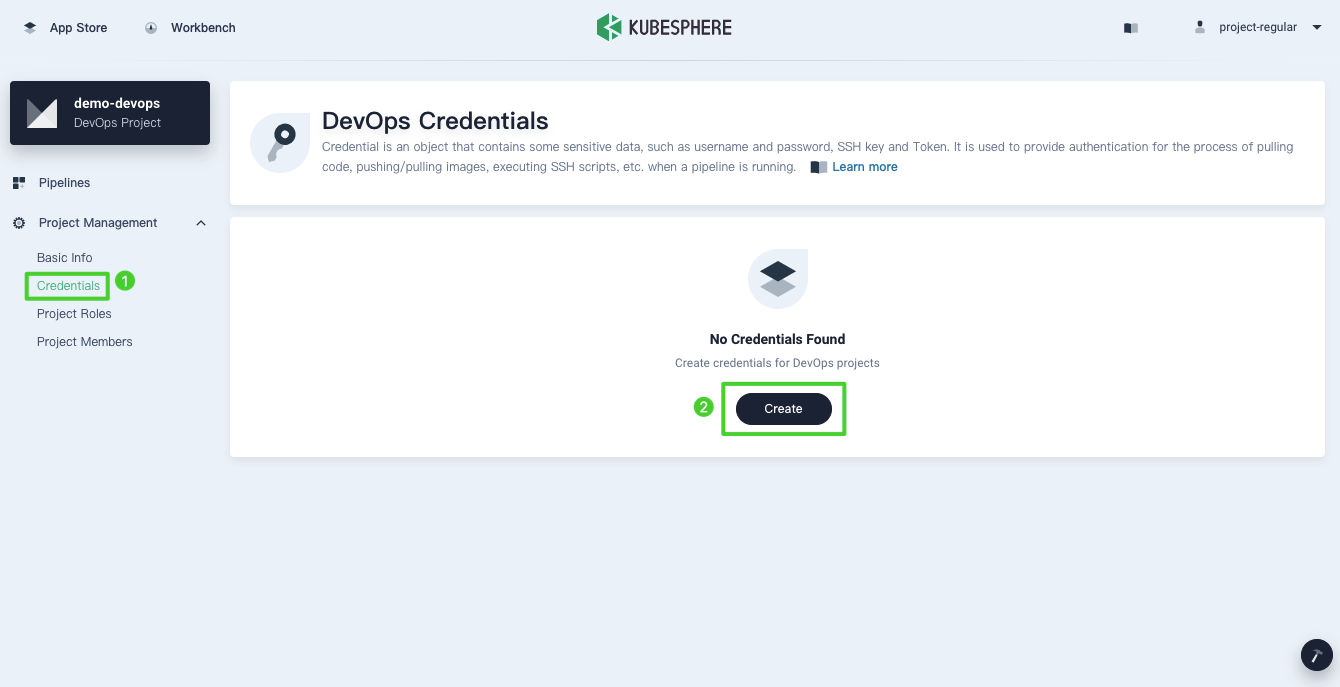
-
On the Create Credentials page, set a credential ID (
robot-test) and select Account Credentials for Type. The Username field must be the same as the value ofnamein the JSON file you just downloaded and input the value oftokenin the file for Token/Password.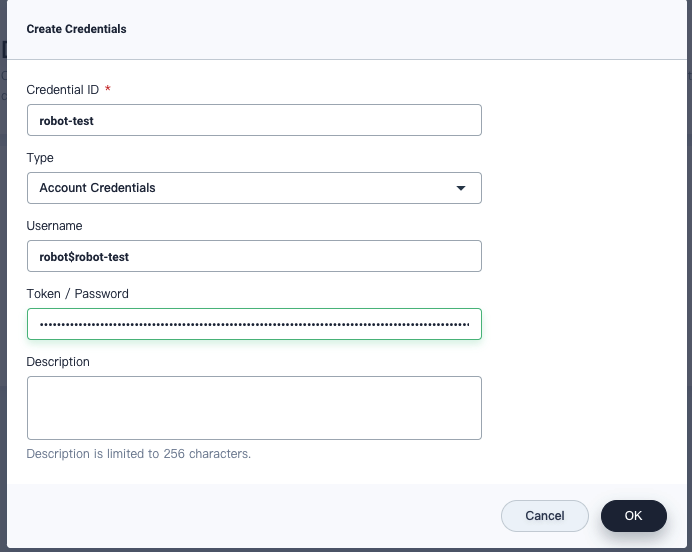
-
Click OK to save it.
Create a Pipeline
-
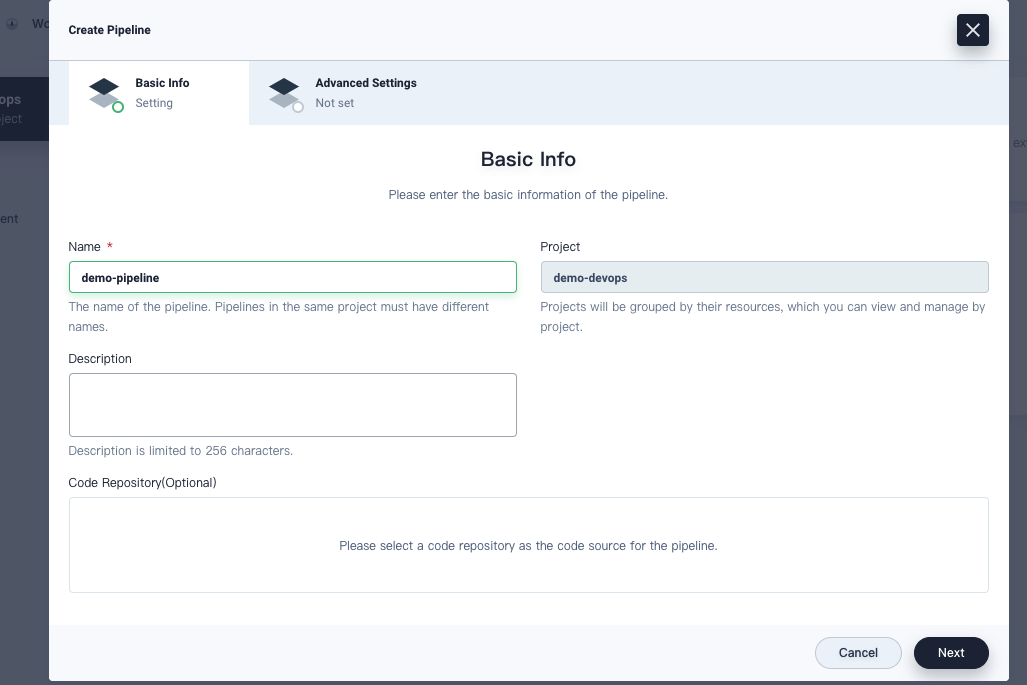
Go to the Pipelines page and click Create. Provide the basic information in the dialog that appears and click Next.
-
Use default values in Advanced Settings and click Create.
Edit the Jenkinsfile
-
Click the pipeline to go to its detail page and click Edit Jenkinsfile.
-
Copy and paste the following contents into the Jenkinsfile. Note that you must replace the values of
REGISTRY,HARBOR_NAMESPACE,APP_NAME, andHARBOR_CREDENTIALwith your own values.pipeline { agent { node { label 'maven' } } environment { // the address of your harbor registry REGISTRY = '103.61.38.55:30002' // the project name // make sure your robot account have enough access to the project HARBOR_NAMESPACE = 'ks-devops-harbor' // docker image name APP_NAME = 'docker-example' // ‘robot-test’ is the credential ID you created on the KubeSphere console HARBOR_CREDENTIAL = credentials('robot-test') } stages { stage('docker login') { steps{ container ('maven') { // replace the Docker Hub username behind -u and do not forget ''. You can also use a Docker Hub token. sh '''echo $HARBOR_CREDENTIAL_PSW | docker login $REGISTRY -u 'robot$robot-test' --password-stdin''' } } } stage('build & push') { steps { container ('maven') { sh 'git clone https://github.com/kstaken/dockerfile-examples.git' sh 'cd dockerfile-examples/rethinkdb && docker build -t $REGISTRY/$HARBOR_NAMESPACE/$APP_NAME:devops-test .' sh 'docker push $REGISTRY/$HARBOR_NAMESPACE/$APP_NAME:devops-test' } } } } }Note
You can pass the parameter todocker login -uvia Jenkins credentials with environment variables. However, every Harbor robot account’s username contains a “$” character, which will be converted into “$$” by Jenkins when used by environment variables. Learn more.
Run the Pipeline
Save the Jenkinsfile and KubeSphere automatically creates all stages and steps on the graphical editing panels. Click Run to run the pipeline. If everything goes well, the image will be pushed to your Harbor registry by Jenkins.













 Previous
Previous
