
You are viewing documentation for KubeSphere version:v3.0.0
KubeSphere v3.0.0 documentation is no longer actively maintained. The version you are currently viewing is a static snapshot. For up-to-date documentation, see the latest version.
Credential Management
Credentials are objects containing sensitive information, such as usernames and passwords, SSH keys, and tokens. When a KubeSphere DevOps pipeline is running, it interacts with objects in external environments to perform a series of tasks, including pulling code, pushing and pulling images, and running scripts. During this process, credentials need to be provided accordingly while they do not appear explicitly in the pipeline.
A DevOps project user with necessary permissions can configure credentials for Jenkins pipelines. Once the user adds or configures these credentials in a DevOps project, they can be used in the DevOps project to interact with third-party applications.
Currently, you can store the following 4 types of credentials in a DevOps project:
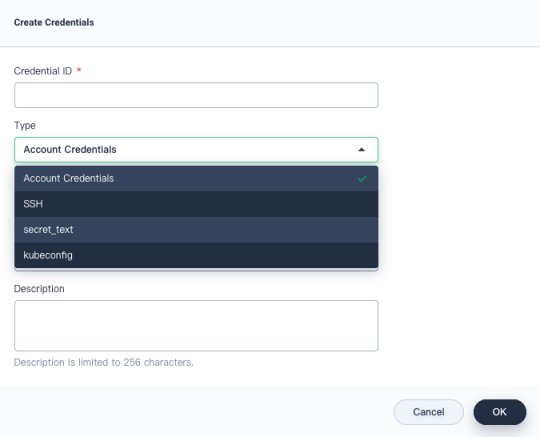
- Account Credentials: Username and password which can be handled as separate components or as a colon-separated string in the format
username:password, such as accounts of GitHub, GitLab, and Docker Hub. - SSH: Username with a private key, an SSH public/private key pair.
- Secret Text: Secret content in a file.
- kubeconfig: It is used to configure cross-cluster authentication. If you select this type, the dialog will auto-populate the field with the kubeconfig file of the current Kubernetes cluster.
This tutorial demonstrates how to create and manage credentials in a DevOps project. For more information about how credentials are used, see Create a Pipeline Using a Jenkinsfile and Create a Pipeline Using Graphical Editing Panels.
Prerequisites
- You have enabled KubeSphere DevOps System.
- You have a workspace, a DevOps project and an account (
project-regular) invited to the DevOps project with theoperatorrole. If they are not ready yet, see Create Workspaces, Projects, Accounts and Roles.
Create Credentials
Log in to the console of KubeSphere as project-regular. Navigate to your DevOps project, choose Credentials and click Create.
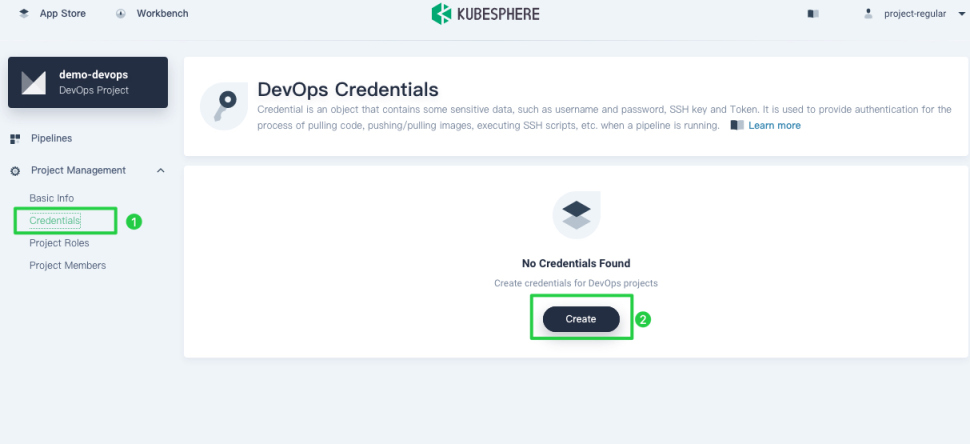
Create Docker Hub credentials
-
In the dialog that appears, provide the following information.
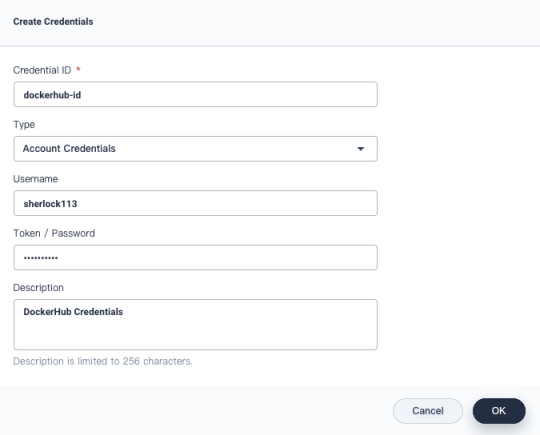
- Credential ID: Set an ID, such as
dockerhub-id, which can be used in pipelines. - Type: Select Account Credentials.
- Username: Your Docker Hub account (i.e Docker ID).
- Token/Password: Your Docker Hub password.
- Description: A brief introduction to the credentials.
- Credential ID: Set an ID, such as
-
Click OK when you finish.
Create GitHub credentials
Similarly, follow the same steps above to create GitHub credentials. Set a different Credential ID (for example, github-id) and also select Account Credentials for Type. Enter your GitHub username and password for Username and Token/Password respectively.
Note
@ and $ in your account or password, they can cause errors as a pipeline runs because they may not be recognized. In this case, you need to encode your account or password on some third-party websites first, such as urlencoder. After that, copy and paste the output for your credential information.Create kubeconfig credentials
Similarly, follow the same steps above to create kubeconfig credentials. Set a different Credential ID (for example, demo-kubeconfig) and select kubeconfig.
Info
View and Manage Credentials
-
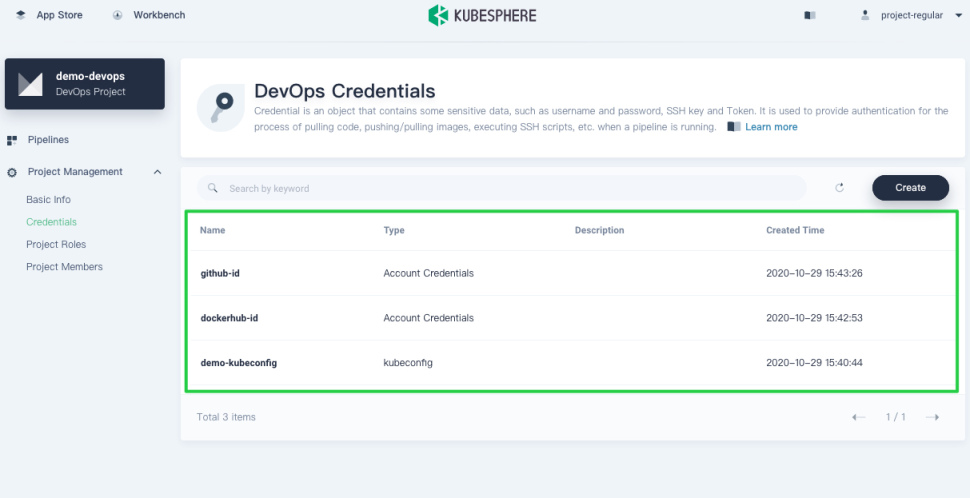
Credentials created display in the list as below.
-
Click any of them to go to its detail page, where you can see account details and all the events related to the credentials.
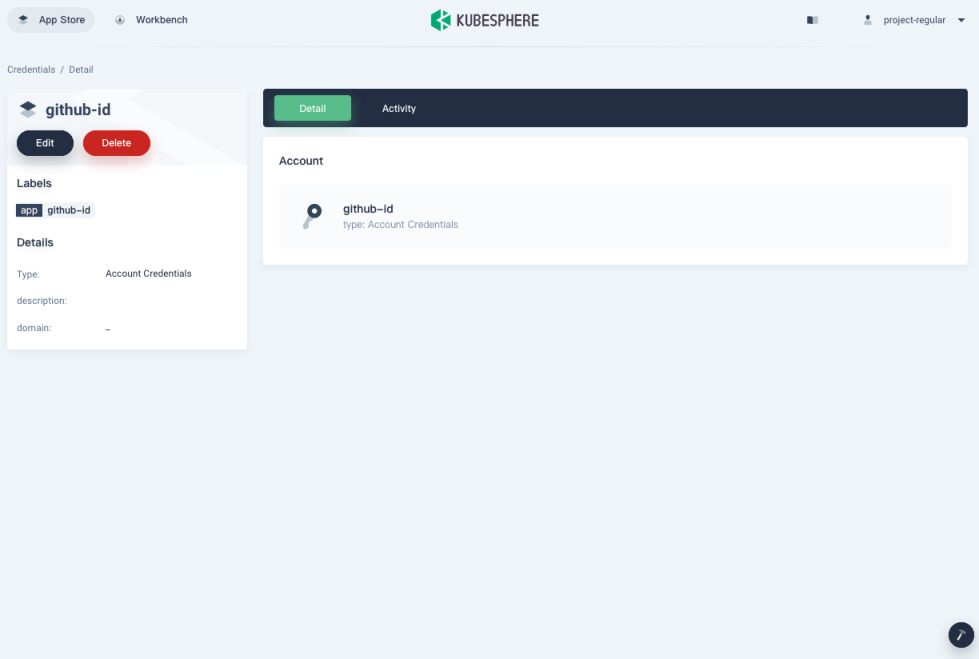
-
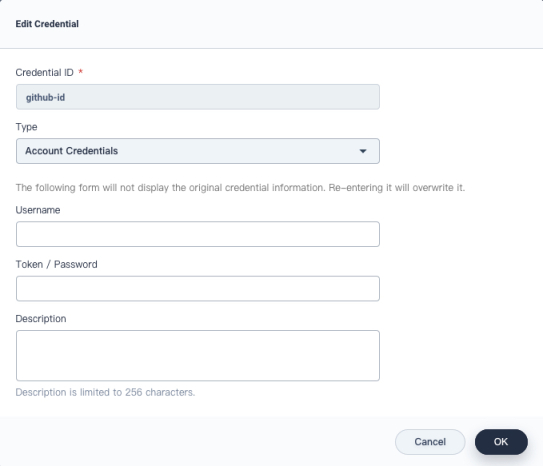
You can also edit or delete credentials on this page. Note that when you edit credentials, KubeSphere does not display the existing username or password information. The previous one will be overwritten if you enter a new username and password.













 Previous
Previous
